Dynamic VLANs
 Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their requirements and initial administrative overhead. As such, most administrators and network engineers tend to prefer Static VLANs.
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their requirements and initial administrative overhead. As such, most administrators and network engineers tend to prefer Static VLANs.
Dynamic VLANs
Dynamic VLANs, as opposed to Static VLANs, do not require the administrator to individually configure each port, but instead, a central server called the VMPS (VLAN Member Policy Server). The VMPS is used to handle the on-the-spot port configuration of every switch participating on the VLAN network.
The VMPS server contains a database of all workstation MAC addresses, along with the associated VLAN the MAC address belongs to. This way, we essentially have a VLAN-to-MAC address mapping:
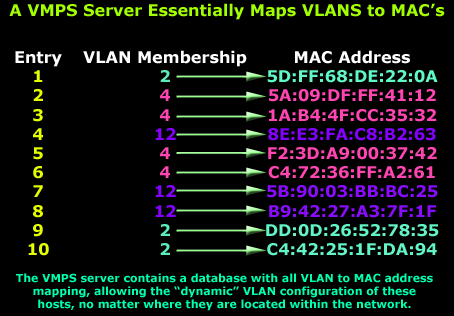
The above diagram works as an aim to help us understand the mapping relationship that exists in the VMPS server. As shown, each MAC address, which translates to a host on the network, is mapped to a VLAN, allowing this host to move inside the network, connecting to any switch that is part of the VMPS network and maintain its VLAN configuration.
You can now start to imagine the initial workload involved when configuring a VMPS server for a network of over 300 workstations:)
As one would expect, the above model works very well and also requires the switches to be in constant contact with the VMPS server, requesting configuration information everytime a host connects to a switch participating in the VLAN network. Of course, there is a lot more information we can use to configure the VMPS database, but we won't be covering that just as yet.
Like all network services offered, Cisco has cleverly designed this model to be as flexible as our network might require. For example, you are able to connect more than one host on one dynamically configured port, as long as all hosts are part of the same VLAN:
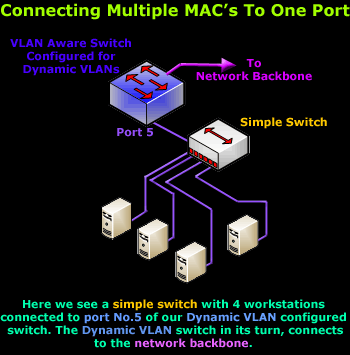
The diagram above shows us a VLAN capable switch that has been configured to support Dynamic VLANs. On port No.5, we have connected a simple switch (not VLAN aware) from which another 4 workstations are connected.
As mentioned previously, this type of configuration is valid and therefore supported, but it also has its restrictions and limitations.
One of the restrictions, which by the way can also be considered as a semi-security feature, is that all workstations connected to the same port, must be configured in the VMPS server as part of the same VLAN, otherwise the port is most likely to shut down as a security precaution.
To consider the limitations of this configuration: if the switch detects more than 20 active hosts (20 MAC addresses) on the port, it will once again shut it down, leaving the workstations without any network connection. When this happens, the port that shuts down will return into an isolated state, not belonging to any VLAN.
The fact is that Dynamic VLANs are really not suitable for every network, even though they allow a great deal of flexibility and security. If you consider the advantage one single feature of Dynamic VLANs can provide you with, then it might be all you need to implement them.
Because each host connected to the switch is checked against the VMPS database for its VLAN membership before the port is activated and assigned to a VLAN, this gives the network administrator the ability to ensure no foreign host is able to walk up to a wall socket and simply plug their workstation to access the network, if his MAC address is not stored in the VMPS database. For a large scale network, this could be considered an ACE card under your sleeve.
Choosing Correct Switches
One important factor we haven't yet mentioned is that you cannot run the VMPS server on a Cisco Catalyst 2900 or 3500 series. The Catalyst 4500 and upwards are able to act as a VMPS, and at the time of writing, this switch has reached its end of retail life. For those who have dealt with Cisco Catalyst switches in the past, you would know that a Catalyst 4500 is not the type of switch you would use in a 20 or 50 node network!
The Catalyst 4500, 6500 series, are switches designed for enterprise networks, as such, they are built to be modular, easily expandable depending on your needs, and lastly, fully redundant because you can't have your core backbone switch failing when all other switches and network equipment are directly connected to it.
We've added a few pictures of the Catalyst 6500 series for you to admire :)

You can clearly see the slots available that allow the Catalyst switches to expand and grow with your network. In the likely event you require more ports as your network expands, you simply buy a Fastethernet blade (some people call them 'slices') and insert it into an available slot!
Dynamic VLANs & FallBack VLANs
Another very interesting and smart feature Dynamic VLANs support is the fallback VLAN. This neat feature allows you to automatically configure a port to a VLAN specially created for workstations whose MAC address is not in the VMPS server. Consider company visitors or clients who require specific or restricted access to your network, they can freely connect to the network and have Internet access, alongside with limited rights on public directories.
In the event the fallback VLAN has not been configured and the MAC address connected to the switch's port is unknown, the VMPS server will send an 'access-denied' response, blocking access to the network, but the port will remain active. If the VMPS server is running in 'secure-mode', it will proceed and shutdown the port as an additional security measure.
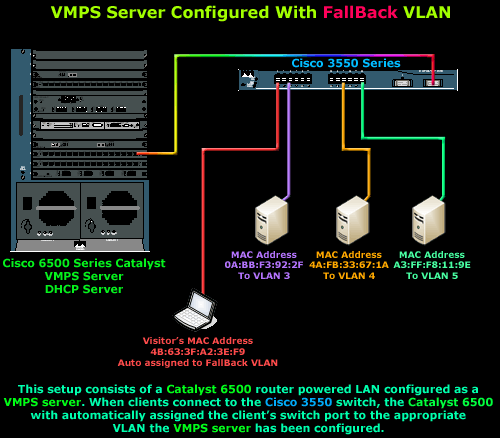
The above diagram represents a portion of a large scale network using a Cisco 6500 Catalyst as the core switch. The switch has been configured to support Dynamic VLANs, therefore a VMPS server has been configured inside the switch, alongside with a DHCP server for each created VLAN. The administrator has already assigned the 3 workstations MAC addresses to the VLANs shown and also created the fallback VLAN for any MAC address that does not exist in the database.
Now consider this interesting scenario: One morning a visitor arrives in the office and requires Internet connection so he can demonstate a new product to the management. As an administrator, you've already configured a fallback VLAN with a DHCP server activated for the VLAN, pushing the necessary settings to the clients so they may obtain Internet access services.
The visitor finds a free RJ-45 socket on the wall, which connects to a Catalyst 3550 switch nearby, and plugs in his laptop. Before the user is allowed to access the network, the Cisco 3550 switch checks the laptop's MAC address and reads 4B:63:3F:A2:3E:F9. At this point, the port is blocked, not allowing the laptop computer to send or receive data. The Cisco 3550 switch sends the MAC address to the 6500 Catalyst switch which is acting as the VMPS server and it checks for an entry that matches the specified MAC address but is unable to find one.
Naturally, it determines that this a visitor, so it creates an entry for that MAC address to the fallback VLAN and sends the information back to the Cisco 3550 switch. The switch will then enable access to the port our visitor is connected to by configuring the port to the fallback VLAN.
If the visitor's computer is configured to obtain an IP Address automatically, it will do so, once the operating system has booted. When this happens, the visitor's DHCP request will arrive to the 6500 Catalyst switch and its DHCP server will send the requested information, enabling the client (our visitor) to configure itself with all the parameters required to access the VLAN. This will also mean our visitor is now able to access the Internet!
Finishing, if the computer is not configured for DHCP, the client must be advised with the correct network settings or asked to enable automatic IP configuration in their network properties.
Summary
The past pages could be considered as an 'eye-opener' for people who are new to the VLAN concept, and at the same time a 'quick-overview' for those who are well aware of their existence! We hope all your questions to this point have been answered, if not, they are most likely too advanced and will surely be answered in the pages that follow.
Previous - Static VLANs
Your IP address:
18.226.181.49
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!


















