Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
ISDN Layers, Protocols & Components
| Read |
|
Articles:
Introduction To The ISDN Protocol
| Read |
|
Articles:
Introduction To Protocols
| Read |
|
Articles:
File Transfer Protocol - FTP
| Read |
|
Articles:
Trivial File Transport Protocol - TFTP
| Read |
|
Articles:
IPSec - Internet Protocol Security
| Read |
Suggested Articles:
Network Address Translation - NAT
Dynamic NAT - Part 1
Dynamic NAT is the second NAT mode we're going to talk about. Dynamic NAT, like Static NAT, is not that common in smaller networks but you'll find it…
Ethernet Protocol, CSMA/CD, Collisions
Ethernet Troubleshooting - Physical Frame Corrupt…
When troubleshooting your Ethernet network, the first thing to look for is physical frame corruption. In this essay, we will discuss the different ca…

Network Fundamentals
Securing Your Home Network
In today's world, securing your home network is more important than ever. With the increasing number of cyberattacks, data breaches, and online fraud…
Network Protocols
Understanding the Need for IPv6 - How IPv6 Overco…
Internet has been around in its current form since the 1980s. What started off as an in-house project in ARPA in 1958 rapidly expanded into what we k…
Featured Subcategories:
Netflow Articles:
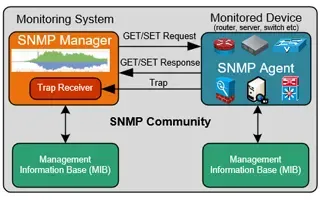
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
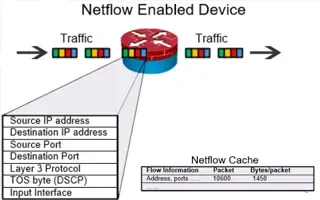
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and securit…

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of their…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…
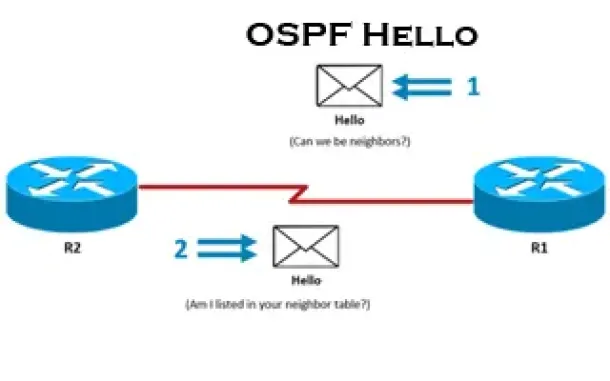
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
Routing
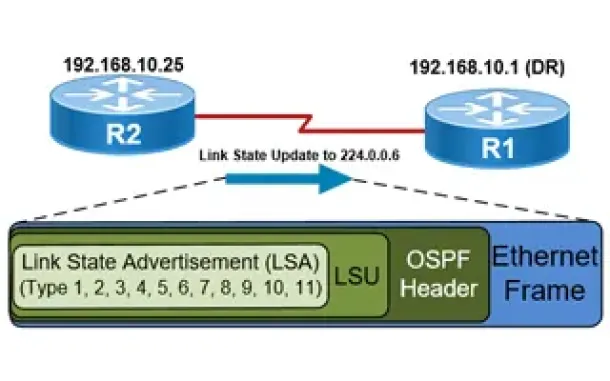
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
Routing
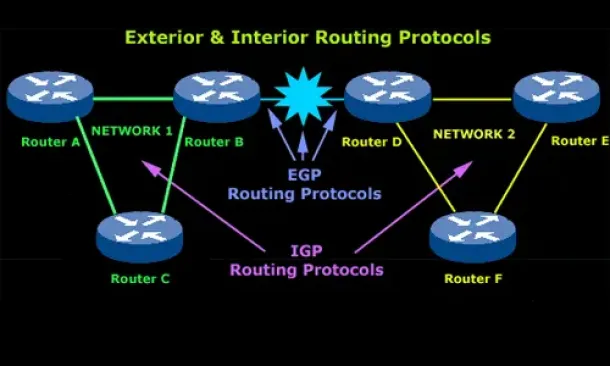
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
Routing
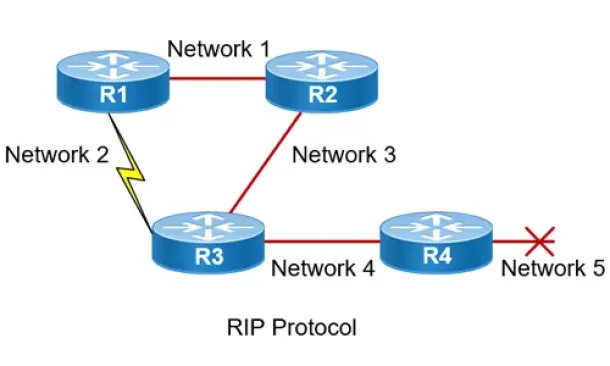
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Cisco Wireless
Easily Convert Cisco Autonomous - Standalone AP to Lig…
This article explains how to convert a local or remote Autonomous / Standalone Cisco Aironet Access Point to Lightweight and register it to a Cisco WLC Co…
Cisco Firewalls
Cisco ASA5500 (5505, 5510, 5520, etc) Series Firewall…
The Cisco ASA 5500 series security appliances have been around for quite some time and are amongst the most popular hardware firewalls available in the ma…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roaming pr…



















