DoS & DDoS Attacks
 A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a website, server or network by flooding it with traffic or overloading its resources. The aim of such an attack is to make the targeted system unavailable to legitimate users, resulting in a denial of service.
A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a website, server or network by flooding it with traffic or overloading its resources. The aim of such an attack is to make the targeted system unavailable to legitimate users, resulting in a denial of service.
A Distributed Denial of Service (DDoS) attack is a type of DoS attack that is carried out by multiple devices, such as computers or smartphones, that are coordinated by a single attacker or group of attackers. This type of attack is more sophisticated and difficult to mitigate because it originates from a large number of sources, making it challenging to identify and block the attacking traffic. DDoS attacks can be launched using a variety of techniques, including botnets, amplification attacks, and application-layer attacks. These attacks have become a significant threat to businesses, organizations, and individuals as they can cause significant financial losses, reputational damage, and even result in the loss of sensitive data. Therefore, it is essential to implement robust security measures to protect against these attacks.
Denial of Service Attacks
Denial of Service (DoS) attacks can be a serious federal crime with penalties that include years of imprisonment and many countries have laws that attempt to protect against this. At the very least, offenders routinely lose their Internet Service Provider (ISP) accounts, get suspended if school resources are involved, etc.
There are two types of DoS attacks:
- Application-based attacks.
- Network-based attacks.
Let's take a closer look at each type of attack.
Application-based Attacks
These attacks target the applications or services running on a system, such as a web server or database, with the aim of overloading them or exploiting vulnerabilities to crash the system. Some examples of application-based attacks include HTTP flooding, where the attacker sends a large number of HTTP requests to the target, or buffer overflow attacks, where the attacker exploits a vulnerability in the application to overload the system's memory.
Developers, Security engineers and Cybersecurity specilists often use special software such as Web Application Vulnerability Scanners to scan and identify application-level vulnerabilities, and patch them before hackers find and exploit them.
Networking Attacks
These attacks target the network infrastructure of a system, such as routers, switches, or firewalls, with the aim of overwhelming them with traffic. This can be achieved through techniques such as flooding, where the attacker sends a large number of packets to the target, or through a ping flood, where the attacker sends a large number of ping requests to the target, causing it to become unresponsive. Other flooding methods include UDP or TCP SYN packets.
Spoofing attacks involve the attacker disguising their IP address to make it appear as if the attack is coming from a different source. This technique can be used to bypass filters and access control mechanisms, making it difficult for defenders to trace the source of the attack.
Amplification attacks are a more sophisticated type of network-based DoS attack. In these attacks, the attacker exploits a vulnerability in a third-party system to generate a large amount of traffic and direct it to the target system. This can be achieved through techniques such as DNS amplification, NTP amplification, or SNMP reflection.
Defending against network-based DoS attacks requires a multi-layered approach that includes firewalls, intrusion detection systems, and traffic filtering. Additionally, organizations can use techniques such as rate-limiting, blacklisting, and IP blocking to mitigate the effects of these attacks. Regular security audits and updates to network devices and software can also help reduce the risk of network-based DoS attacks.
Distributed Denial-of-Service
A distributed denial-of-service (DDoS) attack is similair to the DoS attack described above, but involves a multitude of compromised systems which attack a single target, thereby causing denial of service for users of the targeted system. The flood of incoming messages to the target system essentially forces it to shut down, thereby denying service to the system to legitimate users.
A hacker (or, if you prefer, cracker) begins a DDoS attack by exploiting a vulnerability in one computer system and making it the DDoS "master." It is from the master system that the intruder identifies and communicates with other systems that can be compromised. The intruder loads cracking tools available on the Internet on multiple -- sometimes thousands of -- compromised systems. With a single command, the intruder instructs the controlled machines to launch one of many flood attacks against a specified target. The result of these packets which are sent to the target causes a denial of service.
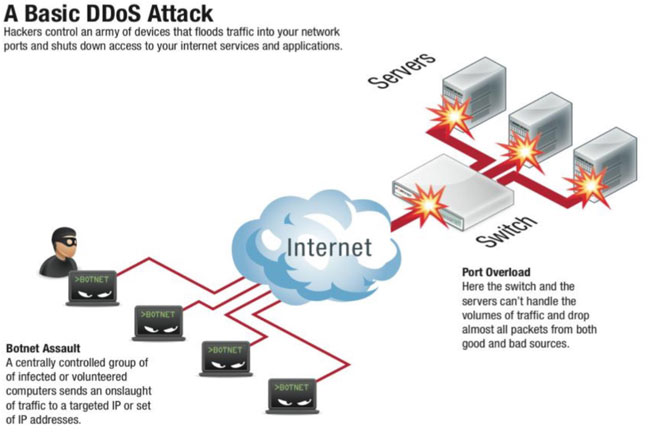
While the press tends to focus on the target of DDoS attacks as the victim, in reality there are many victims in a DDoS attack -- the final target and as well the systems controlled by the intruder.
Implications of DoS and DDoS attacks
Denial of Service (DoS) attacks can have severe implications on organizations, including financial losses, reputational damage, and disruption of business operations. Some of the main implications of a DoS attack include:
Revenue loss: If an organization's website or online services are unavailable due to a DoS attack, it can result in revenue loss. This is particularly true for e-commerce businesses that rely on their online presence to generate sales.
Damage to reputation: A DoS attack can damage an organization's reputation, especially if it results in prolonged downtime or data breaches. Customers may lose trust in the organization's ability to protect their data and may choose to take their business elsewhere.
Business disruption: DoS attacks can disrupt business operations, causing significant delays and downtime. This can affect the productivity of employees and disrupt the supply chain, leading to additional losses.
Data loss or theft: In some cases, DoS attacks can be a smokescreen for more sophisticated attacks such as data theft. Attackers can use the DoS attack to distract security personnel while they attempt to steal sensitive data.
Legal and regulatory consequences: If an organization is unable to protect its customers' data, it can face legal and regulatory consequences, such as fines or legal action.
It is crucial for organizations to have robust security measures in place to protect against DoS attacks, such as firewalls, intrusion detection systems, and regular security audits. In addition, organizations should have a contingency plan in place to ensure business continuity in the event of a DoS attack.
Your IP address:
52.14.6.145
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!


















