Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
|
Articles:
802.3 Fast Ethernet (100 Mbit/Sec) Model
| Read |
|
Articles:
Migrating From Ethernet To Fast Ethernet
| Read |
| Read | |
| Read | |
|
Articles:
The Novell Proprietary Frame Format
| Read |
|
Articles:
The IEEE 802.3 SNAP Frame Format
| Read |
|
Articles:
The Ethernet II Frame Format
| Read |
|
Articles:
The IEEE 802.3 Frame Format
| Read |
|
Articles:
Manchester Signal Encoding
| Read |
|
Articles:
IEEE 802.3 Interframe Spacing
| Read |
| Read | |
|
Articles:
Propagation Delay
| Read |
|
Articles:
Late Ethernet Collisions
| Read |
|
Articles:
Early Ethernet Collisions
| Read |
|
Articles:
Introduction to Ethernet Collisions
| Read |
|
Articles:
What is CSMA/CD ?
| Read |
Suggested Articles:
Network Protocols
Understanding the Need for IPv6 - How IPv6 Overco…
Internet has been around in its current form since the 1980s. What started off as an in-house project in ARPA in 1958 rapidly expanded into what we k…

Network Fundamentals
Securing Your Home Network
In today's world, securing your home network is more important than ever. With the increasing number of cyberattacks, data breaches, and online fraud…
Supernetting & CIDR
Supernetting In-Depth Analysis - Learn to Identif…
Our previous article served as an introduction to Supernetting, also known as Route Summarization. We covered the concept of Supernetting, how it wor…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 4: TCP Flag Options
As we have seen in the previous pages, some TCP segments carry data while others are simple acknowledgements for previously received data. The popula…
Featured Subcategories:
Netflow Articles:

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
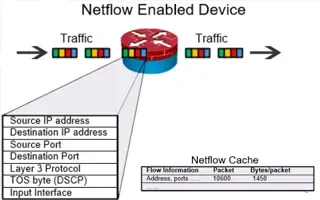
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
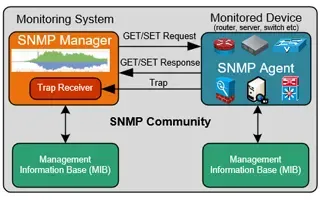
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
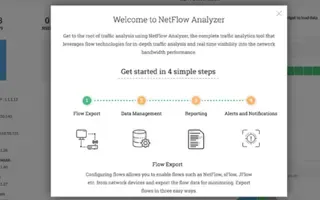
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…
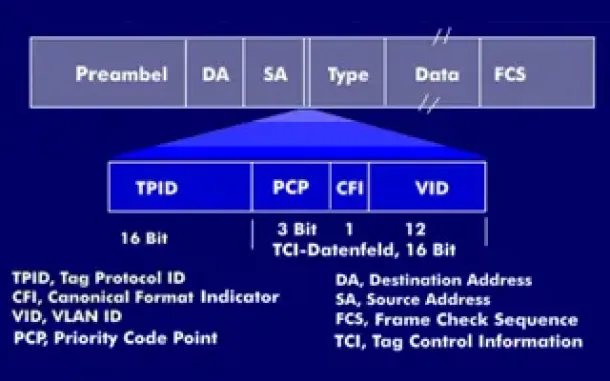
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network wi…
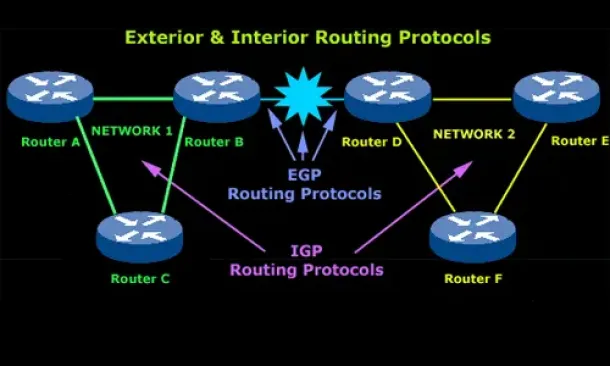
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
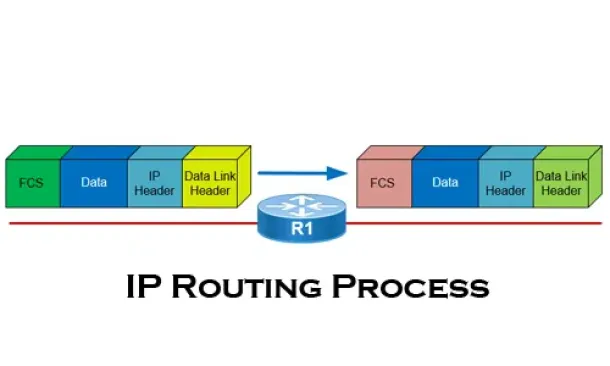
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
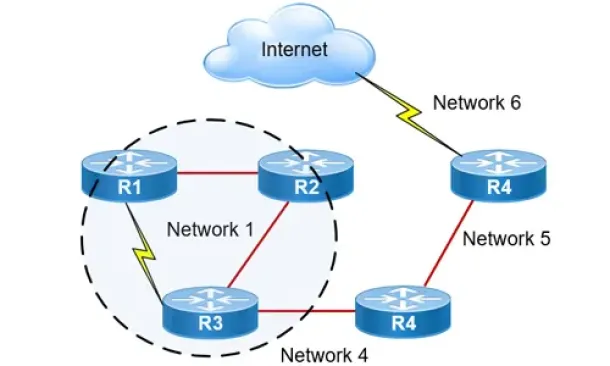
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
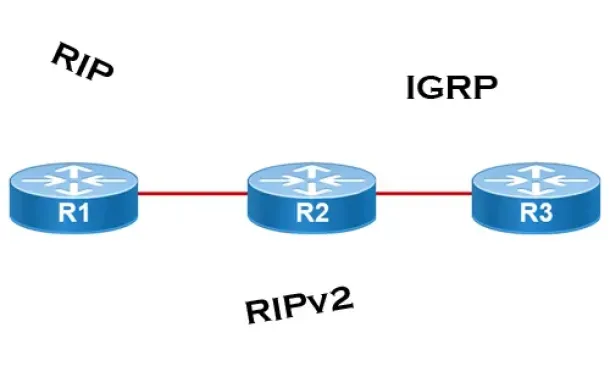
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
Virtualization & VM Backup
FREE Webinar - Fast Track your IT Career with VMware C…
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladder in…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect it wi…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and correct…



















