Network Fundamentals: Top Picks
Network Fundamentals
Securing Your Home Network
In today's world, securing your home network is more important than ever. With the increasing number of cyberattacks, data breaches, and online fraud…
Network Fundamentals
Media Access Control - MAC Addresses
A MAC address, or Media Access Control address, is a unique identifier assigned to a network interface controller (NIC) for use as a network addres…
Network Fundamentals
Measuring Network Performance: Test Network Throu…
Measuring network performance has always been a difficult and unclear task, mainly because most engineers and administrators are unsure which approac…
Network Fundamentals
Controlling Broadcasts and Multicasts
The first step in controlling broadcast and multicast traffic is to identify which devices are involved in a broadcast or multicast storm. The follow…
Featured Subcategories:
Netflow Articles:
Netflow
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Netflow
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Netflow
Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
Netflow
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Network Protocols:
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 1: TCP Source & Des…
This section contains one of the most well-known fields in the TCP header, the Source and Destination port numbers. These fields are used to specify…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 2: TCP Sequence & A…
This page will closely examine the Sequence and Acknowledgement numbers. The very purpose of their existence is related directly to the fact that the…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 6: TCP Options
The TCP Options (MSS, Window Scaling, Selective Acknowledgements, Timestamps, Nop) are located at the end of the TCP Header which is also why they ar…
Domain Name System (DNS)
The DNS Protocol - Part 1: Introduction
If you ever wondered where DNS came from, this is your chance to find out ! The quick summary on DNS's history will also help you understand why DNS…
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 4: TCP Flag Options
As we have seen in the previous pages, some TCP segments carry data while others are simple acknowledgements for previously received data. The popula…
Supernetting & CIDR
Supernetting In-Depth Analysis - Learn to Identif…
Our previous article served as an introduction to Supernetting, also known as Route Summarization. We covered the concept of Supernetting, how it wor…
Domain Name System (DNS)
The DNS Protocol - Part 2: DNS Queries & Resoluti…
This section will help you understand how the DNS queries work on the Internet and your home network. There are two ways to use the domain name syste…
Subnetting
IP Subnetting - Part 1: The Basic Concepts
When we subnet a network, we basically split it into smaller networks. For example, when a set of IP Addresses is given to a company, e.g 254 they mi…
STP/ICMP Protocols:
ICMP Protocol
ICMP Protocol - Part 5: Source Quench Message Ana…
The ICMP - Source Quench message is one that can be generated by either a gateway or host. You won't see any such message pop up on your workstation…
ICMP Protocol
ICMP Protocol - Part 4: Destination Unreachable M…
The 'ICMP Destination unreachable' message is quite interesting, because it doesn't actually contain one message, but infact six! This means that the…
ICMP Protocol
ICMP Protocol - Part 6: Redirect Messages
The ICMP - Redirect Message is always sent from a gateway to the host and the example below will illustrate when this is used.
Putting it simply (be…

Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 1: Understand STP P…
One of the most used terms in network is LAN (Local Area Network). It’s a form of network that we encounter in our daily lives, at home, at work, stu…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network wi…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…
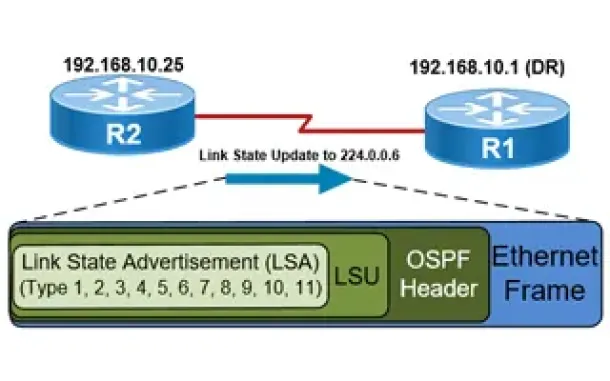
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
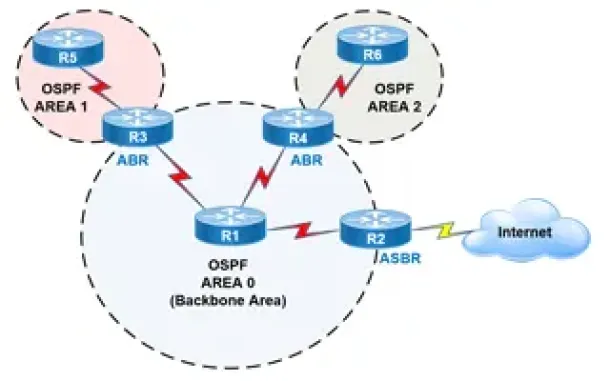
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
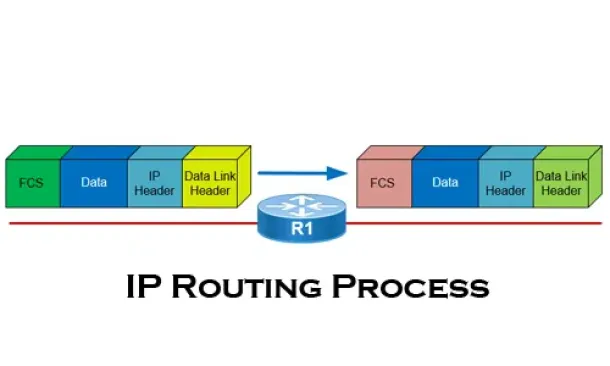
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
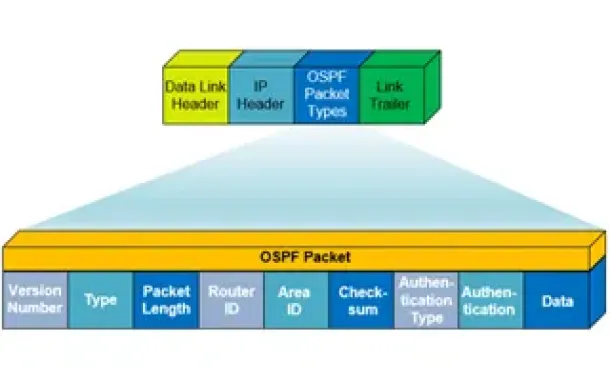
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Network Address Translation - NAT
Static NAT - Part 1
Static NAT (also called inbound mapping) is the first mode we're going to talk about and also happens to be the most uncommon between smaller networks.
S…
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part 1
NAT Overload is the most common NAT method used throughout all networks that connect to the Internet. This is because of the way it functions and the limi…
Network Address Translation - NAT
Dynamic NAT - Part 1
Dynamic NAT is the second NAT mode we're going to talk about. Dynamic NAT, like Static NAT, is not that common in smaller networks but you'll find it used…
Network Address Translation - NAT
Static NAT - Part 2
The previous page (Static NAT - Part 1) helped us understand what exactly happens with Static NAT and how it works, and we saw a few examples of how to us…



















