Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
OpenMosix - Part 5: Testing Your Cluster
| Read |
| Read | |
|
Articles:
OpenMosix - Part 3: Using ClusterKnoppix
| Read |
| Read | |
| Read | |
Suggested Articles:

ManageEngine Firewall Analyzer
Master Your Firewall: 6 Expert-Backed Steps to Bo…
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure yo…
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Featured Subcategories:
WireShark Articles:
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
Your IP address:
3.139.86.227
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
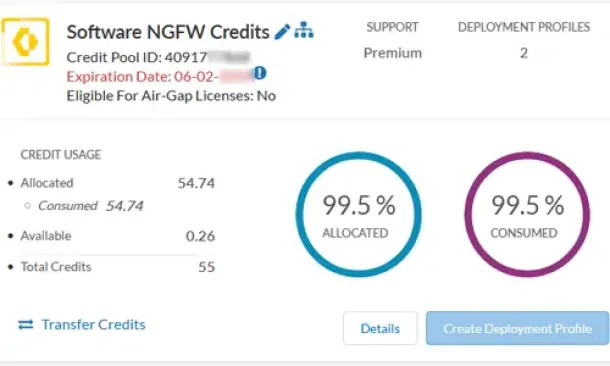
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Windows Servers
Installing Windows Server 2012 Active Directory via Se…
This article serves as an Active Directory tutorial covering installation and setup of a Windows 2012 Domain Controller using Windows Server Manager (GUI)…

Windows Servers
Deploying Active Directory & DNS Services on Windows S…
This article provides a comprehensive guide to deploying Active Directory and DNS Services on Windows Server 2022, encompassing the Essential, Standard, a…
Windows Servers
Windows Server 2012 File Server Resources Manager (FSR…
The Windows Server 2008 first carried FSRM or Fie Server Resources Manager, which allowed administrators to define the file types that users could save to…
Windows Servers
Windows Server Group Policy Link Enforcement, Inherita…
Our previous article explained what Group Policy Objects (GPO) are and showed how group policies can be configured to help control computers and users wit…
Popular Topics

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…

Network Fundamentals
Need for Speed – The Data Tsunami & Advancements in Ne…
A long-long time ago (not long ago in earth time) 100 Mbps was THE technology. 100 Mbps uplinks bundled with ether-channel was the ultimate uplink technol…
Windows Servers
How to Enable ‘Web Server’ Certificate Template Option…
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server. …
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Network Pro…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and inspect…
Cisco CallManager-CCME
Cisco CallManager Express Basic Concepts - Part 1
This article introduces basic CallManager Express (CCME) concepts by covering how a CCME router operates, how calls are setup between Cisco IP phones but…
Cisco Routers
Configuring Dynamic NAT (NAT Overload) On A Cisco Rout…
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the networ…
Cisco Wireless
Wireless (Wifi) WEP WPA WPA2 Key Generator
The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or…
Cisco Wireless
Cisco Aironet 1242AG /1240 - Multiple SSID & 802.1q…
This article explains how the Cisco 1240 series access point can be setup to provide support for multiple SSID, each SSID assigned to a separate…


















