Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Linux File & Folder Permissions
| Read |
|
Articles:
Advanced Linux Commands
| Read |
|
Articles:
Installing Software On Linux
| Read |
|
Articles:
The Linux Command Line
| Read |
|
Articles:
The Linux File System
| Read |
|
Articles:
Why Use Linux?
| Read |
MS Server Articles:
Windows Servers
Simple Guide on Installing & Configuring a Window…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organizati…
Windows Servers
New Features in Windows Server 2012 - Why Upgrad…
There is no doubt that Cloud Computing is hot topic these days. Innovations in cloud computing models have made every industry and company IT departm…
Windows Servers
How to Install and Configure SNMP for Windows Ser…
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device supp…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduce…
Featured Subcategories:
Virtualization & VM Backup Articles:
FREE Webinar - Fast Track your IT Career with VMw…
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladd…
How to Enable or Disable SSH on VMware ESXi via W…
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administra…
The Backup Bible. A Free Complete Guide to Disast…
The Free Backup Bible Complete Edition written by backup expert and Microsoft MVP Eric Siron, is comprised of 200+ pages of actionable content divide…
How to Enable SNMP on VMware ESXi Host & Configur…
In this article we will show you how to enable SNMP on your VMware ESXi host, configure SNMP Community string and configure your ESXi firewall to all…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Finding More Information On The Linux Operating System
Since this document merely scratches the surface when it comes to Linux, you will probably find you have lots of questions and possibly problems. Whether…
Linux - Unix
Linux BIND DNS - Part 2: Configuring db.domain Zone D…
It's time to start creating our zone files. We'll follow the standard format, which is given in the DNS RFCs, in order to keep everything neat and less co…
Linux - Unix
Linux VIM / Vi Editor - Tutorial - Basic & Advanced Fe…
When you are using Vim, you want to know three things - getting in, moving about and getting out. Of course, while doing these three basic operations, you…
Linux - Unix
Linux BIND DNS - Part 3: Configuring The db.192.168.0…
The db.192.168.0 zone data file is the second file we need to create and configure for our BIND DNS server. As outlined in the DNS-BIND Introduction, this…
Popular Topics
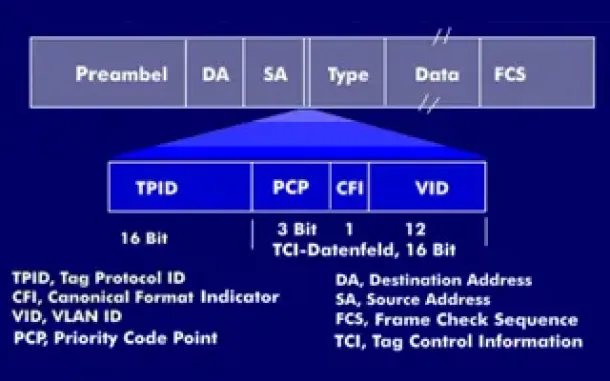
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
Windows Workstations (XP, 7, 8, 10, 11)
How to Start Windows 8 and 8.1 in Safe Mode – Enabling…
This article will show you how to start Windows 8 and Windows 8.1 in Safe Mode and how to enable F8 Safe Mode. Previous Windows O/S users would recall tha…
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network Secur…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/database…
Cisco Routers
How To Configure DNS Server On A Cisco Router
The DNS protocol is used to resolve FQDN (Fully Qualified Domain Names) to IP addresses around the world. This allows us to successfully find and connect…