Acunetix Enterprise: Find Website - Web Application Vulnerabilities & Security Flaws Before Hackers Do
 Security researchers disagree about the percentage of vulnerable websites, but most concur that it’s way too high. Despite their long history, attackers continue to use cross-site scripting (XSS), SQL injection and more to successfully compromise sites and web applications. In today’s era of cloud-based and on-premises web applications that connect directly into the organization - it’s more important than ever to take a step back and consider the risk of web & security vulnerabilities that can leave your organization open to hackers.
Security researchers disagree about the percentage of vulnerable websites, but most concur that it’s way too high. Despite their long history, attackers continue to use cross-site scripting (XSS), SQL injection and more to successfully compromise sites and web applications. In today’s era of cloud-based and on-premises web applications that connect directly into the organization - it’s more important than ever to take a step back and consider the risk of web & security vulnerabilities that can leave your organization open to hackers.
As web applications scale, manual security assessments can become time-consuming and challenging to process while outsourcing these tasks won’t always provide the desired result. In many cases, a degree of automation is the way forward, and the decision becomes which web vulnerability scanner to choose.
Firewall.cx has written extensively about the pros of web vulnerability scanners, popular tools, and good common security practices. Despite this, we keep coming back to Acunetix, and it recently received a major upgrade. Version 12 of the enterprise-grade security tool is a significant leap forward that deserves an in-depth assessment.
Founded in 2005, Acunetix was designed to replicate hackers, yet catch vulnerabilities before they do. The leaps and bounds since its release have led to use in government, military, and banking, as well as partnership with Microsoft and AWS.
Before we dive in our in-depth analysis let’s take a look at the topics covered:
- Installation and Using Acunetix 12 Enterprise
- Scanning Web Applications and Websites with Acunetix 12 Enterprise
- AcuSensor – Achieving 100% High-Severity Vulnerability Accuracy
- Acunetix Reporting, Exporting, and Issue Tracking
- Conclusion
Installing and Using Acunetix 12 Enterprise
When it comes to sheet usability, it’s easy to see why. While most readers will have no problems with complex setups, it’s always nice to avoid the hassle. Acunetix’s installation is a matter of creating an admin account, entering the license key, and choosing a port.
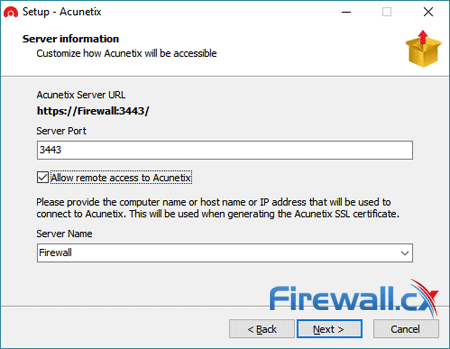
All told, it took a matter of minutes to get up and running and didn’t require any additional configuration or restarts. For Enterprise customers, multi-engine deployment is also available, allowing for more simultaneous scans. As you’d expect, the setup is a little more complex, but still only requires a single line in command prompt and some additional registration inside Acunetix. Once configured, users can set targets to only scan with a specific engine and can push past the normal limit of 25 simultaneous scans.
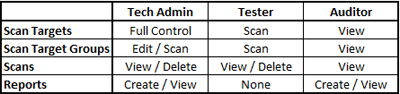
However, many organizations will still want to setup user accounts for different roles. The software has three different account types for Tech Admins, Testers, and Auditors:
Adding additional users is possible via a tab in the settings menu, with an email and secure password with special characters required. After selecting a role, the admin can decide whether to give users access to all targets or add them to a specific target group at a later date.
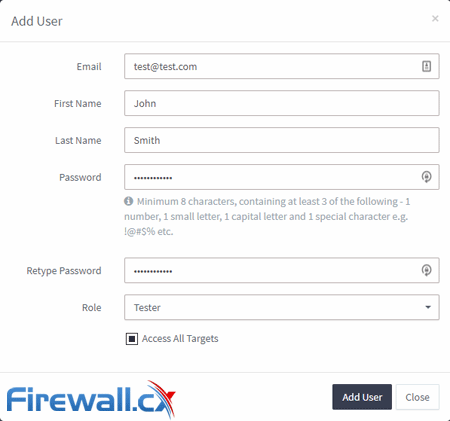
Standard licenses are limited to one user, but Enterprise and Online plans can make an unlimited number, all with separate roles and targets. For additional security, admins can enable two-factor authentication, enforce password changes, and specify the amount of login failures before lockout.
Scanning Web Applications and Websites with Acunetix 12 Enterprise
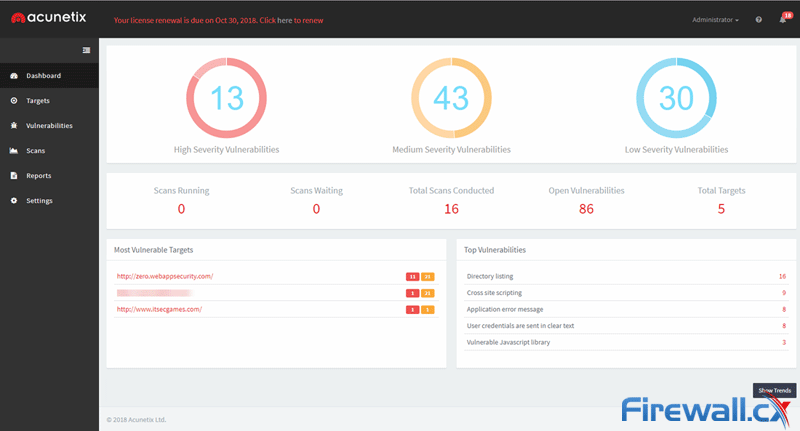
After installation, Acunetix’s web portal opens in the default browser. Users are taken to the dashboard, which reveals the number of open vulnerabilities discovered, websites scanned, and most common vulnerabilities.
Click to enlarge
Users are able to click on the High, Medium, and be taken straight to the Vulnerabilities section for a detailed breakdown. They can click through to specific websites, vulnerability types, and active/waiting scans. It’s a fairly comprehensive overview, and it gets more interesting when you hit the show trends button.
Here, Acunetix gives some long-term metrics. Line graphs show the number of open vulnerabilities in a 12-month period, the average number of days to remediate issues, issues over time, and more.
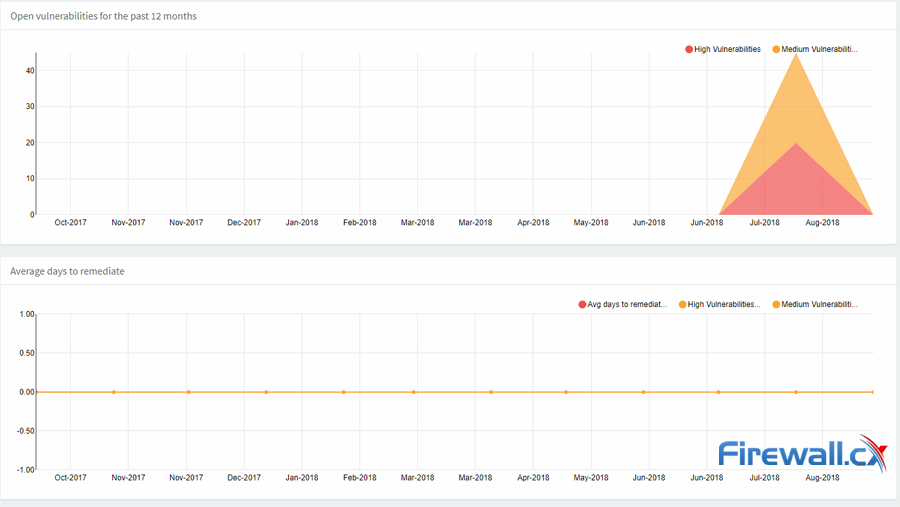
However, though the dashboard presents a nice overview, core functionality is found under the Targets heading. Users are able to click the Add Target button and enter and website or application URL with a description for easy identification.
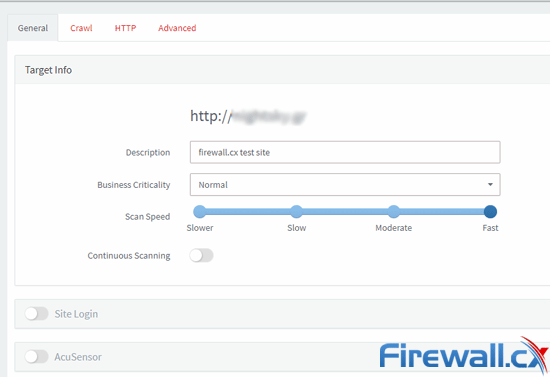
Acunetix then presents you with a number of options, separated into General, Crawl, HTTP, and Advanced tabs. The general tab lets you specify the business criticality of the target, which helps to prioritize the vulnerabilities it detects. You can also set the speed of the scan and choose to scan continuously to monitor the progress long-term. If a scan is taking too long, you can pause it and continue at a later date.
With advanced options, you can specify the languages to scan, add custom headers and cookies, and specify allowed hosts. There’s also the ability to import files for the crawler, such as URL lists and Fiddler Proxy Export. You can even craft custom scan types to look for recently disclosed vulnerabilities.
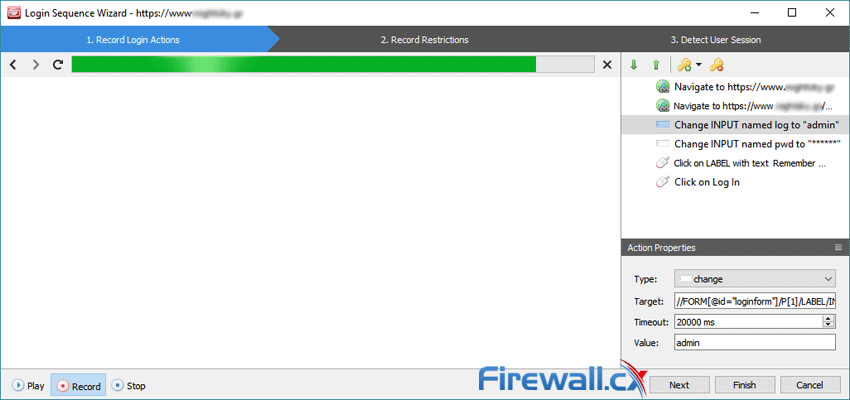
The search section also houses the site login option, which gives the app access to restricted areas for better scanning. In most cases, Acunetix can login to the site automatically, but there’s also an option to record your login sequences via a dedicated sequence wizard.
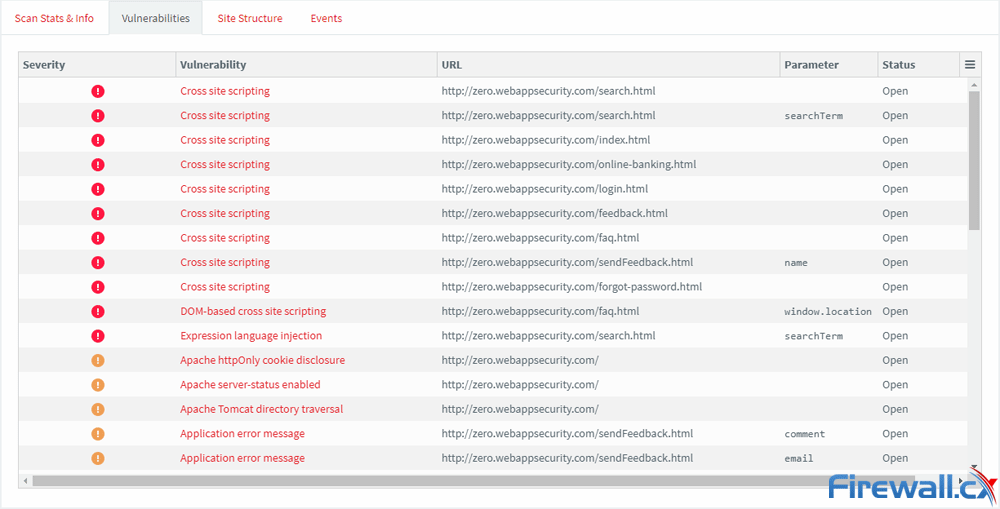
It seems Acunetix has thought of pretty much everything here, and a scan of known test sites revealed many types of issues. It was adept and discovering several instances of cross-site scripting, as well as expression language injection and DOM-based XSS.
Importantly, though, it was also able to find issues that weren’t as critical. Medium severity issues such as Apache httpOnly cookie disclosure, HTML injection, vulnerable Javascript libraries and more were all discovered. Acuentix has made several improvements to their scan times, and we found scans to take no more than 15 minutes even on large sites and with a slow connection.
As mentioned earlier, you can drill down into specific vulnerabilities for more information. A page will give an explanation of the vulnerability, the details of the attack, HTTP requests, and impact. Critically, there’s also information about how to fix the issue, as well as a CWE link and CVSS information. Once reviewed, you can mark them as fixed, ignored, or false positive.
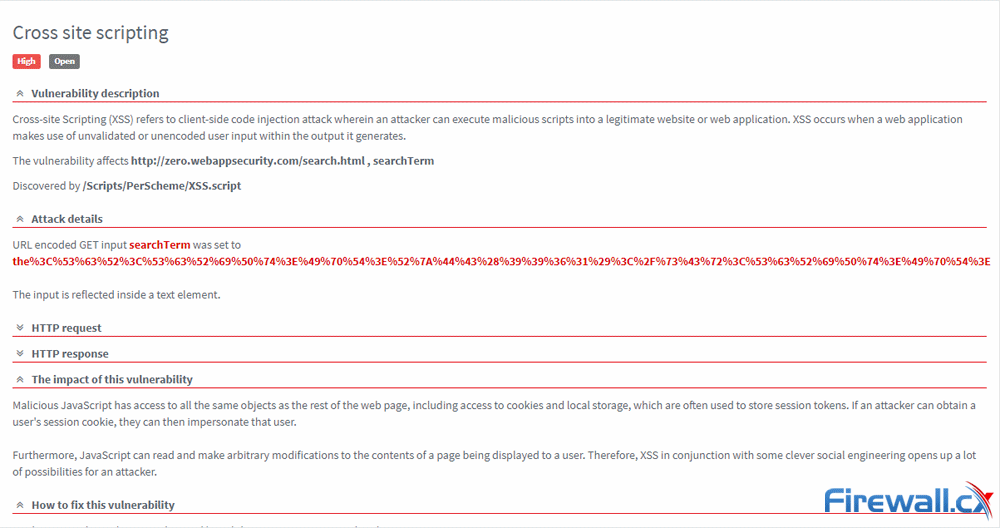
You’re also able to look at vulnerabilities from a site vulnerability perspective, looking at the status of individual files and the specific parameters within them.
AcuSensor – Achieving 100% High-Severity Vulnerability Accuracy
Despite all this, Acunetix emphasises that its users will get better results with the use of AcuSensor. The AcuSensor agent is available for installation on the website in PHP, .NET, and Java form, and improves the accuracy of the scan with better crawling and detection, and well as a decrease in false positives. The company promises a 100% high-severity vulnerability accuracy and detection of a larger range of SQL injection issues.
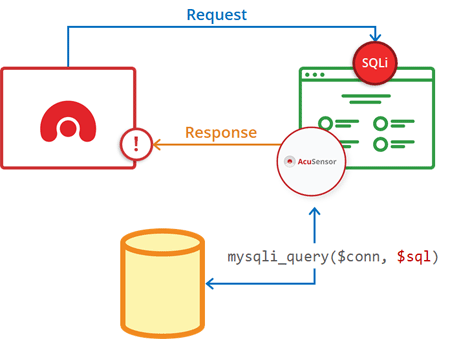
The tool also gives line-of-code information for PHP applications and stack traces for ASP.NET and Java, as well as example SQL queries for injections. This makes it a very powerful offering, though it isn’t recommended for production environments.
Via a Jenkins plugin, the Enterprise variant can also be implemented in continuous integration processes. Jenkins can automatically trigger scans and reports with each build, creating both PDF Acunetix versions and an HTML Jenkins one. It can also fail builds if a certain threat level is reached. There’s a REST API for other integrations, with up-to-the-minute status of ongoing scans, vulnerability details, and more.
Acunetix Reporting, Exporting, and Issue Tracking
Once a scan is complete, users have several options of how to proceed. A strong point of Acunetix is its support for a number of Web Application Firewalls. The software’s WAF Export option supports a number of major solutions, including F5, Imperva, and Fortinet. For others, there’s the choice to export as a regular XML, but that’s only available if you export a full scan. For specific vulnerabilities, you’ll have to use one of the other formats.
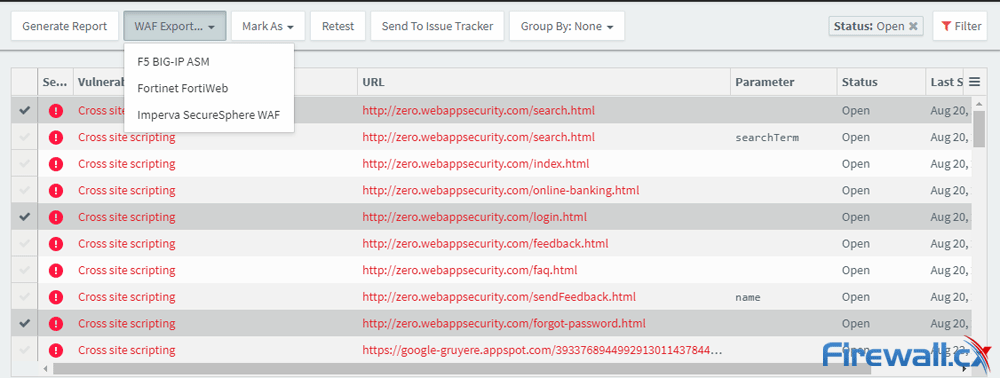
Perhaps more useful is the ability to send vulnerabilities to an issue tracker, though it does have to be configured first. After finding the option, you add GitHub login details and selecting the relevant project. There’s the option to specify an issue type, as well as validate the connection before exiting.
You then have to set up the tracker to with every site by heading back to Targets menu and changing the advanced option. It’s a little clunky to add the option retroactively, but it gets the job done.
In Firewall.cx’s testing, the issues pushed to GitHub near-instantly, with relevant labels and all of the information provided. That includes the target URL, severity, attack details, HTTP requests, impact, remediation suggestions, and references. It all works with a single button press and we have no doubt this will greatly speed up workflows.
Similar functionality exists for JIRA and Microsoft TFS, though JIRA currently has a limit of 20 issue tracker items. It’s generally smart during the process, refusing to open duplicate issues for the most part.
Overall, the issue tracker capabilities are quite impressive and intuitive, but there are options for traditional reporting if your organization requires it. There a number of standard templates, but also a total of ten different compliance templates, which is extremely useful.
Reports are available in PDF or HTML for CWE 2011, HIPAA, ISO 27001, OWASP, and more. Each starts with an explanation and continues with a category-by-category breakdown with the number of alerts and information about each.
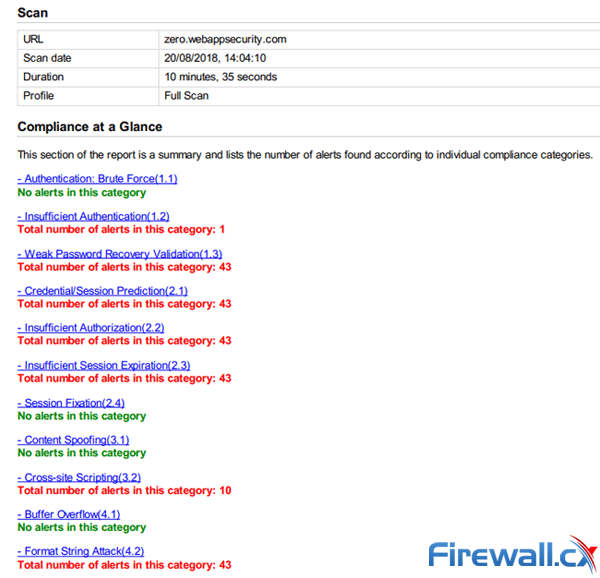
There’s no real room for customisation here, but there’s little need for it. Everything you’d expect is covered, and displayed in a logical, if not particularly pretty way. Reports generate quickly in the background and can be produced on a per-scan, per-target, or bulk basis.
Conclusion
Firewall.cx first began its journey with Acunetix began almost 12 years ago with its standalone Windows 98 program. The distance the web vulnerability scanner has come since then is truly immeasurable, managing to keep up with the competition as other companies have faded into the background.
The product sports a minimal and modern UI, but its results aren’t to be scoffed at, being the only one to net out-of-band vulnerabilities. Its long time in the industry has allowed it to think of pretty much everything, with no major drawbacks to speak of and new integrations in the works. Though report design is average, the number of templates is higher than usual, and many will lean on its issue tracker support.
Thanks to Acunetix Enterprise v12, organizations are now able to scan in-house, third-party and cloud-based web applications or websites for security vulnerabilities such as SQL injections, Cross-Site Scripting attacks, hundreds of other security flaws, and take corrective action. Developers can automate vulnerability assessments in their processes, achieve 100% high-severity vulnerability accuracy thanks to AcuSensor and detect of a larger range of SQL injection issues. Compliance reports can be generated to suite CWE 2011, HIPAA, ISO 27001, OWASP standards and much more.
Despite this significant feature set, it remains affordable to all ogranizations and is well worth looking into. An Enterprise Plus plan also available, offering over 20 targets at a variable price.
Your IP address:
3.21.28.69
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!