Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Firewall.cx Free Cisco Lab: Our Partners
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…

EventLog Analyzer
Event Log Monitoring System: Implementation, Chal…
An event log monitoring system, often referred to as an event log management, is a critical component to IT security & Management, that helps org…

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…
OpManager - Network Monitoring & Management
Network Management Systems Help Businesses Accura…
Accurately monitoring your organization’s business application performance, service provider SLA breaches, network infrastructure traffic, bandwidth…
Featured Subcategories:
WireShark Articles:
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Your IP address:
3.19.237.16
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…
Windows Servers
Understanding, Creating, Configuring & Applying Window…
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover…
Windows Servers
New Features in Windows Server 2012 - Why Upgrade to…
There is no doubt that Cloud Computing is hot topic these days. Innovations in cloud computing models have made every industry and company IT departments…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
Free Hyper-V eBook - Create, Manage and Troubleshoot Y…
With the introduction of Hyper-V on the Windows Server platform, virtualization has quickly become the de facto standard for all companies seeking to cons…
Popular Topics
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
Network Fundamentals
The Importance of a Network Analyzer – Packet Sniffer…
Network Analyzers, also known as Packet Sniffers, are amongst the most popular network tools found inside any Network Engineer’s toolkit. A Network Analyz…
Network Protocol Analyzers
Advanced Network Protocol Analyzer Review: Colasoft Ca…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review, the…
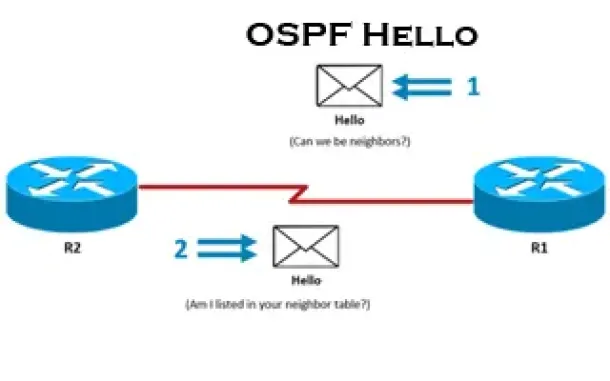
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
Cisco Wireless
Understanding, Configuring & Tweaking Web-based Cisco…
Cisco Aironet Access Points, just like most Cisco devices, provide a web interface from which we are able to configure the device. It is often we are pres…
Cisco Services & Technologies
Comparing Cisco VPN Technologies – Policy Based vs Rou…
Virtual Private Networks constitute a hot topic in networking because they provide low cost and secure communications between sites (site-to-site VPNs) wh…
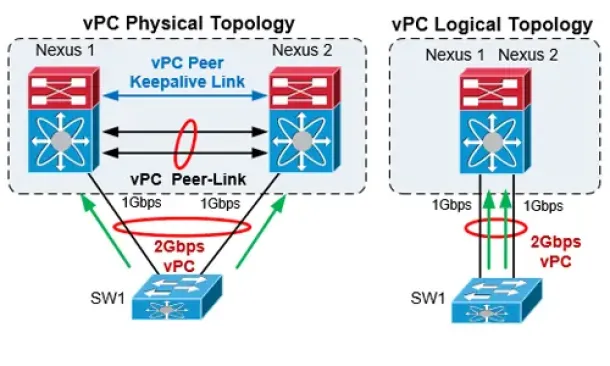
Cisco Data Center (Nexus/UCS)
The Complete Cisco Nexus vPC Guide. Features & Advanta…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different Cisco…
Cisco Routers
Troubleshooting PPP Internet Connection On A Cisco Rou…
The Point-to-Point Protocol is one of the most popular protocols around used by engineers, ISPs and companies around the globe for authentication of remot…


















