Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into OpM…
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberattac…

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…
Featured Subcategories:
WireShark Articles:
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Your IP address:
3.138.141.138
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
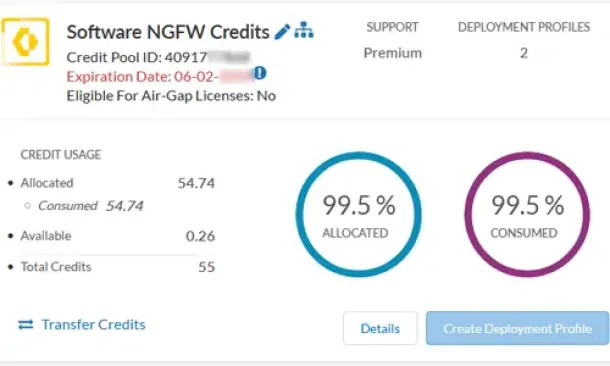
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Windows Servers
New Upcoming Features in Hyper-V vNext - Free Trainin…
With the release of Hyper-V vNext just around the corner, Altaro has organized a Free webinar that will take you right into the new Hyper-V vNext release…
Windows Servers
Introduction To Windows Server 2012 R2 Virtualization…
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Virtualization is an abstraction layer that…
Windows Servers
Installing Active Directory Services & Domain Controll…
This article serves as an Active Directory tutorial covering installation and setup of Windows 2012 Active Directory Services Role & Domain Controller…
Windows Servers
How to Recover & Create "Show Desktop" Icon Function o…
The Show Desktop feature, included with almost all versions of Windows up to Windows 7, allows a user to minimize or restore all open programs and easily…
Popular Topics
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…

Network Fundamentals
Network Unicast - Its role and Importance
Unicast is a communication method used in computer networking where data is sent from a single sender to a specific destination device. In this meth…

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative overhe…
Windows Servers
Windows 2003 DNS Server Installation & Configuration
DNS is used for translating host names to IP addresses and the reverse, for both private and public networks (i.e.: the Internet). DNS does this by using…
Cisco Routers
Cisco Router 'User Exec' Mode
Introduction
Let's see what it looks like to be in User-Exec mode on a Cisco router. Below, we have telneted into our lab router and are in User Exec Mod…
Cisco Wireless
Cisco Aironet 1242AG /1240 - Multiple SSID & 802.1q…
This article explains how the Cisco 1240 series access point can be setup to provide support for multiple SSID, each SSID assigned to a separate…
Cisco Switches
Installation and Setup of Cisco SG500-52P - 500 Series…
The SG500 series Cisco switches are the next step up from the already popular SG300 Layer-3 switches. Cisco introduced the SG Small Business series switch…
Cisco CallManager-CCME
Cisco Small Business SPA500 IP Phone Series Administra…
Firewall.cx readers can now access and freely download the Cisco Small Business Administration Guide for Cisco SPA500 series IP phones. The Adminis…


















