Complete Guide to SD-WAN. Technology Benefits, SD-WAN Security, Management, Mobility, VPNs, Architecture & Comparison with Traditional WANs. SD-WAN Providers Feature Checklist.
 SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WAN infrastructure and its management.
SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WAN infrastructure and its management.
SD-WANs are suitable for any organization regardless of their size and location(s). Forget about managing routers, firewalls or proxies, upgrading internet lines, high-cost WAN links, leased lines (MPLS), filtering incoming traffic, public-facing infrastructure, VPNs and mobile clients. SD-WANs provide all the above and allow managers, administrators and IT staff to manage their WAN infrastructure via an intuitive, easy-to-use GUI interface, lowering equipment and service contract costs but also minimize the need for continuous upgrades and other expensive and time-consuming exercises.
Related articles:
- The Need for a Converged SASE Platform. Converging Network & Security Services with Catonetworks SASE Platform
- How To Secure Your SD-WAN. Comparing DIY, Managed SD-WAN and SD-WAN Cloud Services
- SASE and VPNs: Reconsidering your Mobile Remote Access and Site-to-Site VPN strategy
- Converged SASE Backbone – How Leading SASE Provider, Cato Networks, Reduced Jitter/Latency and Packet Loss by a Factor of 13!
- Key Features of a True Cloud-Native SASE Service. Setting the Right Expectations
The diagram below clearly shows a few of the network and security services leading global SD-WAN providers such as CATO Networks provide to businesses no matter where they are geographically located around the world.
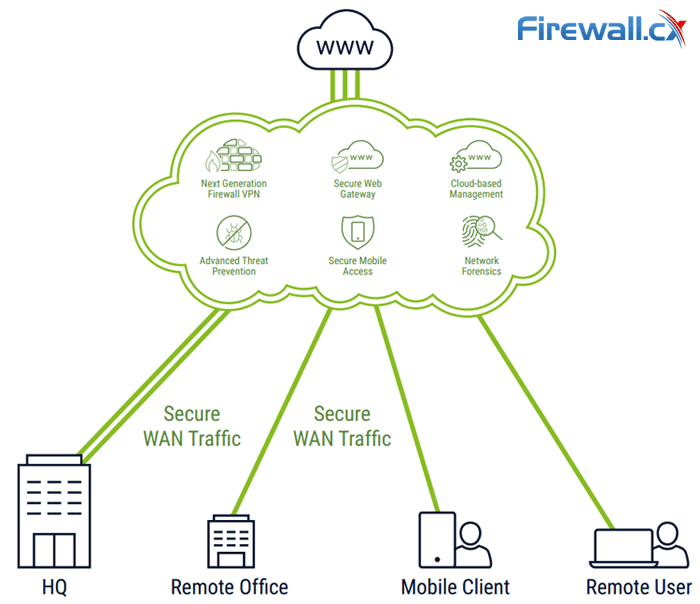
SD-WAN Networks offer zero-touch deployment with advanced network security services
Let’s kick-off this guide by taking a look at the SD-WAN topics covered:
- What is SD-WAN?
- The Problem with Traditional WANs
- How Does SD-WAN Work?
- SD-WAN Benefits
- SD-WAN Architecture
- SD-WAN Architecture - Edge Appliances
- SD-WAN Architecture - Cloud-Based SD-WAN
- SD-WAN Deployment Methods
- SD-WAN Must-Have Features
- Recommended SD-WAN Security & VPN Features
- Recommended SD-WAN Mobility Features
- Recommended SD-WAN Management Features
- Summary
What is SD-WAN?
Software-Defined Wide Area Network (SD-WAN) is a new architectural approach to building Wide Area Networks (WANs) whereby applications and the network configuration are isolated from the underlying networking services (various types of Internet access or private data services sold by network service providers). As a result, the networking services can be reconfigured, added, or removed without impacting the network. The benefits to such an approach address long-standing concerns with traditional WANs around the cost of bandwidth, time to deploy and reconfigure the WAN and more.
The Problem with Traditional WANs
For years, organizations connected their locations with private data services, namely MultiProtocol Label Switching (MPLS) services. Companies contract with their network service provider to place MPLS routers at each location. Those routers connect with one another or a designated site across the MPLS service. MPLS services are seen as being:
- Private because all customer traffic is separated from one another.
- Predictable as the MPLS network is engineered to have very low packet loss
- Reliable as the carrier stands behind the MPLS with service and support, backing it up contractually with uptime (and reliability) guarantees.
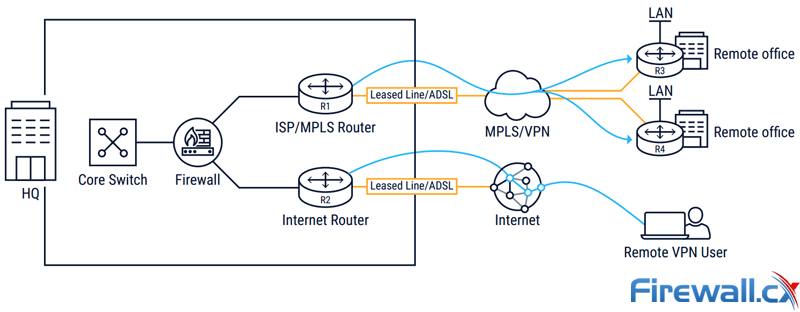
Traditional High-Cost MPLS VPN Networks
As such, MPLS services are expensive (relative to Internet connectivity), in some cases costing 90 percent more than Internet bandwidth. And with bandwidth being so expensive, companies have to be very judicious in their bandwidth usage. Sites are often connected by single MPLS line, creating a potential single point of failure. Delays from line upgrades are a problem, as lines often lack the necessary excess capacity to accommodate traffic changes or new applications. Finally, new deployments take significantly longer than Internet lines — weeks in some cases, months at the extreme — whereas Internet access can be deployed in days if not minutes (with 4G/LTE).
Organizations accepted MPLS limitations for years for numerous reasons. For too long, the Internet was far too erratic to provide the consistent performance needed by enterprise applications. That’s changed significantly within Internet regions over the past few years. A decade ago, most enterprise traffic stayed on the MPLS network, terminating at a headquarters or datacenter housing the company’s applications. Today, Internet and cloud traffic are the norm not the exception, often constituting half of the traffic on and MPLS backbone. The net result is that data transmission costs end up consuming a significant portion of an IT Department’s annual expenditure on its WAN with Internet- and cloud-traffic being a major cause.
How Does SD-WAN Work?
Enter SD-WAN. SD-WAN leverages ubiquitous, inexpensive Internet connections to replace MPLS for much of an organization’s traffic. At a high-level, the SD-WAN separates the applications from the underlying network services. Policies, intelligent routing algorithms, and other technologies in the SD-WAN adapt the network to the application. Depending on implementation, the locations, cloud datacenters, SaaS applications, and mobile users can all be connected into the SD-WAN.
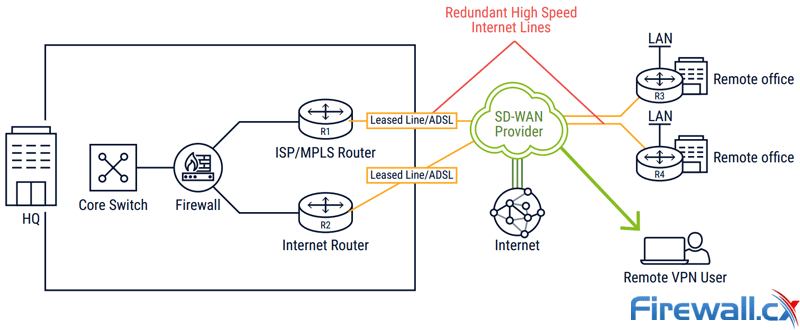
High-Speed Low-Cost SD-WAN with Global SLA Contracts
More specifically, the SD-WAN router sits at the edge of a location’s local network and connects to the network services. Best practices call for at least two connections per location. Hybrid WAN configurations will use an MPLS line and an Internet service, such as fiber, xDSL, cable or 4G/LTE. All-Internet configurations will use two or more Internet service. The SD-WAN routers connect with one another, forming a mesh of encrypted tunnels (the “virtual overlay”) across the underlying network services (the “underlay”), such as cable, xDSL, or 4G/LTE.
Unlike traditional WANs, all lines in an SD-WAN are typically active. The SD-WAN uses Policy-Based Routing (PBR) algorithms and preconfigured application policies to dynamically select the optimum tunnel based on application requirements, business priorities, and real-time network conditions. The SD-WAN is responsible for balancing traffic across the site’s connections. Should there be an outage (a “blackout”) or degradation in the line (a “brownout”), the SD-WAN moves traffic to alternate paths and restores them to initial paths also based on configured policies.
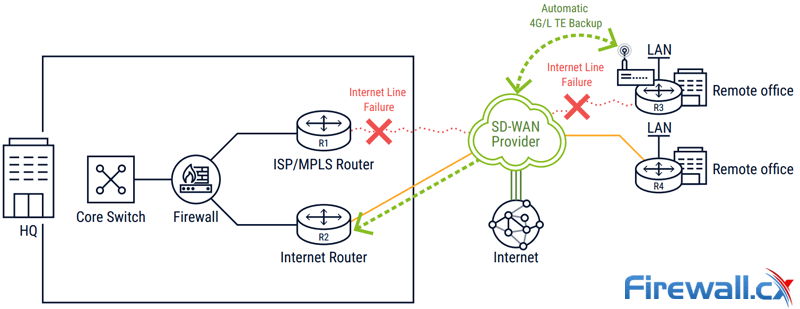
SD-WAN providing alternative connectivity paths during critical line failures
As a result, SD-WAN helps us align our WANs to our business priorities. We can provide every location, user, or resource with just the right available connectivity configured with the just the right amount of resiliency. Business-critical locations, such as a Data Center, can be connected by MPLS and two active, dual-homed connections. Small offices where MPLS may not be available can be connected with one line. Disaster response teams, and other ad-hoc groups, can use 4G/LTE.
Yet despite the configuration, all sites continue to be managed by the same set of security policies and routing rules with the same orchestration engine and from the same management console. In short, we extract maximum value from the underlying WAN resource for optimum Return On Investment (ROI).
SD-WAN Benefits
More specifically, SD-WAN brings benefits to the organization in terms of performance, cost savings, agility, and availability.
SD-WAN Application Performance
Applications have very different networking requirements when it comes to the WAN. Voice is susceptible to jitter and packet loss; bulk data transfers require lots of bandwidth (throughput, actually). Internet routing doesn’t respect those differences. Route selection reflect economic realities between ISPs not application requirements. Internet providers will dump packets on peered networks or keep packets on their own network even though there are “better” routes available.
SD-WAN lets organizations be smarter in how they route traffic. Policies describe the latency, loss and jitter tolerances of various applications. The SD-WAN routers monitor latency, and loss metrics of their connections. They then use that information and the preconfigured policies to select the optimum path for each application.
SD-WAN Cost Savings and Avoidance
Software-Defined Networking (SDN) benefits may still need to be realized in the Data Centers, but they’re very apparent when SDN is applied to the WAN. The ROI of SD-WAN can be dramatic. Internet bandwidth can cost 70 percent less than MPLS bandwidth depending on region and location.
Operational costs are also reduced. Traditional WANs require advanced engineering and mastering of arcane protocols. SD-WANs do not completely eliminate for that experience by any means. But they do help maximize engineering resources by simplifying deployment and management of branch offices. Policy-driven configuration minimizes the amount of “configuration-drift” between branch offices, complicating WAN support. Adding new application services across the WAN without adversely existing services becomes much far easier. Availability requirements can be more readily met.
SD-WAN architectures that include advanced security further improve savings. They eliminate security appliances, saving on the costs related to the upgrading, patching, and maintenance of those appliances.
SD-WAN Availability
The availability of traditional WAN was more often than not determined by the uptime of the last mile. Within the core of the network, service provider have plenty of redundancy. It’s in the connection to the remote site where redundancy is more limited.
Many locations will not have redundant connections. Even if there are redundant connection there’s no guarantee that the physical cabling is fully redundant. The different services may still share some common ducting and cabling, opening the way for a discontinuation of service due to a backhoe severing a line or some other physical plant failure. Running two active connections complicates network engineering. And in the event of a blackout on one connection, failover is rarely fast enough to sustain a session or voice call, for example.
SD-WANs natively improve the availability of locations. Their use of active/active connections builds redundancy into the WAN. By mixing different types of WANs, such as 4G/LTE and fiber, diverse routing becomes easier to guarantee. Should there be a blackout or a brownout, the SD-WAN router automatically switches traffic to the second connection. Depending on implementation, failover can be fast enough to sustain a session; users never realize there’s been a networking issue or link failure.
Agility: Deploying new Sites, Reconfiguring the WAN
SD-WAN allows organizations to respond faster to business conditions. This gets expressed in different ways. Businesses often need to start operations at remote sites quickly or, at least, without extensive delays. Enterprise IT is challenged with deploying networking services and configuring security at remote locations. SD-WAN addresses these problems on several fronts:
Deploying new sites: While provisioning MPLS circuits alone can take up to 90 days, more for high-speed circuits, the Internet circuits used by SD-WAN can be deployed in days, less when considering 4G/LTE connections. While MPLS often required on-site expertise to configure networking equipment, SD-WAN avoids those delays with zero-touch provisioning.
Reconfiguring the WAN: Traditional WAN architectures required the network service provider to change the network, which introduced further delays. If more bandwidth was required at a new location, the service provider had to re-provision the line all of which led to more delay. No wonder Gartner found enterprises to be “...dissatisfied with large incumbent network service providers.” SD-WAN puts the enterprises in control of network provisioning. The use of “fatter” Internet pipes means line provisioning is generally not required.
SD-WAN Architecture
There are two basic SD-WAN architectures, edge appliances and cloud-based SD-WAN. Both edge appliances and cloud-based SD-WAN involve a controller function for pushing out policies and distributing routing information and a management console for dashboard, reporting and policy configuration. Where they differ is in the location of the virtual overlay and how they provide advanced services.
SD-WAN Architecture - Edge Appliances
With edge appliances, the SD-WAN virtual overlay stretches from location to location. Appliances are installed at each site and, once connected to the Internet, retrieve configuration profiles from the SD-WAN controller. The SD-WAN devices configure themselves and joining or construct a virtual overlay with other devices. Each device runs the policy-based routing algorithms needed to steer traffic to the most appropriate link based on application requirements and underlying link quality.
Edge appliance architectures are very familiar to network engineers. It’s been the approach used for years by router vendors, WAN optimization vendors, and more. The approach brings certain known benefits namely:
- Incremental WAN evolution — SD-WAN edge appliances integrate with existing enterprise networking and security infrastructure while making the WAN more agile.
- Transport independence — Edge appliance architectures give customers maximum freedom in choosing network service providers.
At the same time, edge appliance architectures introduce several constraints into the SD-WAN such as:
- Limited ability to improve Internet performance — SD-WAN edge appliances cannot control the end-to-end routing across the Internet. As such, they remain dependent on MPLS to deliver latency- and loss-sensitive applications, particularly across global connections.
- Unable to evolve WAN functionality — The limited capacity of the SD-WAN edge appliance restricts the overlay's capabilities. Advanced security functions, such as decrypting traffic or running extensive rule sets, consume significant resources. Taking full advantage of these features forces an unexpected hardware upgrade. It's the same problem that had long limited the use of unified threat management (UTM) appliances.
- Overly site focused — Appliances are well suited for connecting locations, but they do not naturally extend to support cloud datacenters, SaaS applications, and mobile users. There’s no easy way to place an SD-WAN appliance in the cloud. Mobile users are rarely happy with the poor performance that results when having to connect back to an appliance that could be very far away, particularly when traveling.
SD-WAN Architecture - Cloud-Based SD-WAN
With Cloud-based SD-WAN, the virtual overlay is formed between the points of presence (PoPs) of the Cloud SD-WAN service. The PoPs connect to each other across a privately managed backbone. There are appliances at each location, but in contrast to edge architecture, Cloud-based SD-WAN appliance run “just enough” functionality to send traffic to the nearest PoP. Software in the PoP applies the necessary security and network optimizations before forwarding the traffic along the optimum path to its destination.
Cloud-based SD-WAN is a new approach to networking, but very familiar one to any IT person. It's the same approach used by AWS, Azure and countless other cloud providers. The architectural benefits include:
- Thin edge flexibility — Since the edge appliance needs minimal functionality, the software can be implemented across a wider range of endpoints. Client software, for example, can connect mobile devices into the SD-WAN. The same is true for cloud applications and cloud datacenters.
- Enhanced functionality — By leveraging the resources of the cloud, cloud-based SD-WAN can deliver a broad range of advanced functionality without facing scaling constraints. Network throughput is also be improved by carrying traffic over a private, cloud backbone and not the public internet.
At the same time, cloud-based SD-WAN architectures face several constraints including:
- Education — Converging networking, security, and mobility into the cloud represents a radical transformation in networking. It may require some training for IT professionals to grasp the full implications of the evolution.
- Service Delivery — Cloud-based SD-WAN should be manageable by the customer to avoid the delays and per-task-pricing associated with managed service offerings from carriers and traditional network service providers.
- Geographic Footprint — The effectiveness of Cloud-based SD-WAN services rides on the reach of its network. Without a global network, a Cloud-based SD-WAN service cannot fix the Internet’s consistency, latency and packet loss problems, problems that are particularly prevalent between Internet regions.
Cloud-based SD-WAN is fundamentally different from two other similar sounding solutions (see table):
- Cloud-managed services host the management/orchestration engine in the cloud. The SD-WAN fabric is still constructed from an edge appliance architecture.
- Cloud-hosted services (also called “cloud-delivered”) move some SD-WAN functionality to the cloud. In addition to running the management/orchestration engine in the cloud, some shared infrastructure among customers, such as gateways to cloud services, will run in the cloud. The SD-WAN fabric continues to be constructed edge-to-edge by edge appliances (and gateways).
By contrast, Cloud-based SD-WAN services move the management/orchestration engine, and the SD-WAN fabric into the cloud. Edge appliances (or mobile client software) only implement the critical edge functions to connect to the SD-WAN fabric in the cloud. As such, the shared infrastructure includes not only the gateways on a cloud-hosted service but also full SD-WAN software and the middle-mile transport connecting the POPs.
| CLOUD SD-WAN SERVICES COMPARED | |||
|
|
Location of Management / Orchestration Engine |
Location of Virtual Overlay |
Use of Shared Infrastructure |
|
Cloud-Managed Services |
Cloud |
Appliances |
None |
|
Cloud-Hosted Services |
Cloud |
Appliances |
Partial |
|
Cloud-based Services |
Cloud |
Cloud |
Full |
SD-WAN Deployment Methods
As we’ve seen, organizations can deploy SD-WANs themselves using SD-WAN edge appliances, in what’s sometimes referred to as “Do It Yourself” (DIY) deployments, and cloud-based SD-WANs
In addition to the two primary SD-WAN architectures, service providers offer managed SD-WAN services. As with any managed IT services, managed SD-WAN services repackage vendor’s SD-WAN technology (typically an SD-WAN edge appliance, but not necessarily), with the service providers implementation expertise.
With managed SD-WAN services, organizations rely on the service provider to maintain and run the SD-WAN. As such, there are several service-specific features to consider including:
Service Level Agreements (SLAs) governing all aspects of the service. SLAs should include a detailed description, specify the time needed to make any moves, adds, or changes (MACs) to the SD-WAN. Penalties should be specified as well.
Service and Support - A detailed description of support levels should be provided including escalation procedures and any agreements around time to repair.
Delivery Timeline - A clear project and delivery timeline should be specified with the SD-WAN roll out.
SD-WAN Must-Have Features
There are many features to consider when selecting an SD-WAN edge appliance or cloud-based SD-WAN architecture. The following are the minimum criteria for an SD-WAN:
Endpoints — The SD-WAN solution must connect locations to the SD-WAN with a hardware appliance or software, such as a virtual appliance or a VNF. The SD-WAN solution should also connect other types of resources, namely cloud datacenters (IaaS), cloud applications (SaaS), and mobile users.
Encrypted overlay —-The SD-WAN must establish a secure, virtual overlay across network services. All traffic across that overlay must be encrypted. The overlay must be policy-driven.
Data service independence —- The SD-WAN must connect locations with major types of Internet data services, such as fiber, xDSL, cable, and 4G/LTE, and MPLS, for hybrid deployments.
Application policies — The SD-WAN must provide configurable policies describing application characteristics, such as failover options and the minimum and maximum thresholds for latency, loss, and jitter.
Real-time line monitoring — The SD-WAN appliances must able to gather real-time latency and packet loss statistics of the attached lines.
Policy-based routing — The SD-WAN must implement algorithms that can select the optimum route for a given application based on configured application policies and real-time line statistics.
Recommended SD-WAN Security & VPN Features
While it’s not a definitional requirement, the SD-WAN solution should include advanced security services. All SD-WAN providers claim to deliver a “secure SD-WAN” but that only refers to traffic protection. Organizations still need to protect against data exfiltration, malware infection, and other advanced security threats, which requires advanced security technologies such as Next-Generation Firewall (NGFW), Secure Web Gateway (SWG), and advanced threat protection.
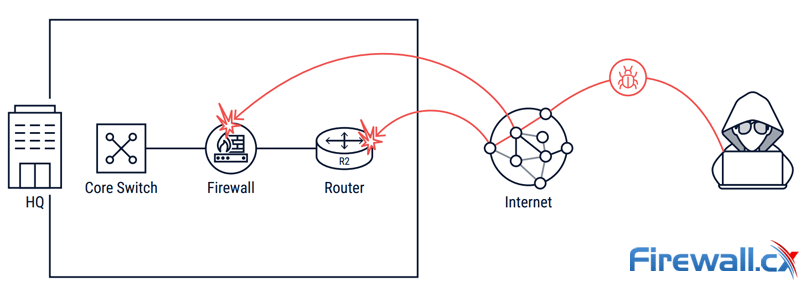
Companies are forced to deal with internet & malware attacks to their infrastructure
Ideally, the SD-WAN will be converged with the advanced security services. With security and networking converged together, deployment becomes much simpler, capital costs drop, and operationally, the SD-WAN and security infrastructure are easier to maintain than with separate security and networking devices. But if converged security is not possible, at the very least the SD-WAN provider should offer service chaining/insertion to integrate with external third-party security services.
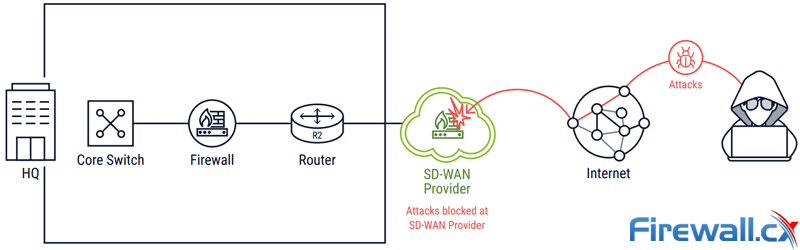
SD-WAN providers block all malicious traffic/attacks at the Cloud level
Deployment costs will be higher and operations more complex than with a converged SD-WAN, but that’s necessary. Much of performance and cost benefits of an SD-WAN come from replacing MPLS access with direct Internet access at the branch office. By exiting Internet traffic locally, the SD-WAN avoids the backhaul and performance problems of traditional WAN configurations. Without advanced security at the branch office, users can’t take advantage of local Internet and remain immune to the range of Internet-borne threats.
Specific advanced security features to consider from an SD-WAN provider include:
Next-Generation Firewall (NGFW)
The NGFW should offer:
- High performance and elasticity — Inspect all application traffic, regardless of volume or use of encryption, without forced capacity upgrades.
- Application awareness — Identify access to on-premise or cloud applications regardless of the port or protocol being used, or if the application is SSL encrypted.
- User awareness — Identify users, groups, and locations regardless of IP address
- Unified, granular security policy — Control access to applications, servers and network resources
Secure Web Gateway (SWG)
The SWG should offer:
- Dynamic site classification — The SWG capabilities should Include a URL database with many site category classifications including phishing, malware delivery, botnets and other malicious sites.
- Block, prompt or track user access — The Reduce legal or security exposure from risky web usage
- Web access policy enforcement — Restrict website access in accordance with a corporate policy
Advanced Threat Prevention
The advanced threat protection capabilities should include:
- Anti-malware — Scan HTTP and HTTPS traffic for malicious files and stop endpoint infections.
- IPS / IDS — Applies context-aware protection to traffic based on domain / IP reputation, geolocation, known vulnerabilities, DNS, as well as application- and user-awareness.
SD-WAN offers three options for delivering advanced security functions at the branch - local security appliances, virtual network function, or firewall as a service (FWaaS):
Local Security Appliances
Local Security Appliances such as firewall or UTM appliances, are the typical way companies protect branches. Appliances notorious for introducing operational complexity and increasing costs. There’s significant overhead incurred from configuring, patching and maintaining security appliances at each location. And, as mentioned above, using advanced security functions (or continuing to operate effectively when traffic levels spike), requires the use of significant hardware resources from the appliance. Often security professionals end up choosing between disabling advanced features, compromising organizational security, or being forced into a hardware upgrade.
Virtual Network Function (VNF)
VNF is a virtual network security stack deployed into a physical SD-WAN appliance or third-party applianced called a vCPE. As such, VNFs reduce the physical challenges of running separate physical boxes at the branch office — the HVAC issue, calculating power, and the rest of the wiring closet issues. However, VNFs are still discrete entities, requiring management of their software and upgrades, and facing the same scaling issues as any local security appliance.
Firewall as a Service (FWaaS)
Firewall as a Service (FWaaS) faces none of the scaling and maintenance challenges of local security appliance or VNFs. The infrastructure was built from the ground up as a cloud service, eliminating the management challenges and scaling issues of security appliances. They do require the service provider to offer a fully multitenant, easy-to-use, and powerful security engine that can be run fully by the customer.
Recommended SD-WAN Mobility Features
The SD-WAN was classically seen as a replacement to the WAN and, as such, did not focus on connecting mobility. But with data and applications shifting to the cloud, any SD-WAN should connect mobile and stationary users to those resources.
To do so, the SD-WAN should equip mobile users with client software for securely connecting into the SD-WAN. Once connected to the SD-WAN, the mobile user should be supported with the same optimized routing, security policies and management controls as users located within the office. Specific features should include:
Automatic optimum path selection — The SD-WAN mobile client should should dynamically select the optimum path to the closest SD-WAN node (closest PoP).
Access control — Once connected to the SD-WAN, fine-grained access controls should restrict mobile user access by application, active directory groups or specific user identity. Organizations should be able to determine the precise resources that can be seen and accessed by the mobile user.
Advanced security — Mobile users should be fully protected by any advanced security services provided by the SD-WAN, such as NGFW, IPS, and SWG.
Recommended SD-WAN Management Features
The management and administration console is the view into the SD-WAN. As such, usability and design are obviously critical.
In the example below, the CATO Networks SD-WAN management interface provides an intuitive interface from where we can monitor, configure policies and manage the entire WAN network without worrying about service providers, VPNs or network equipment!
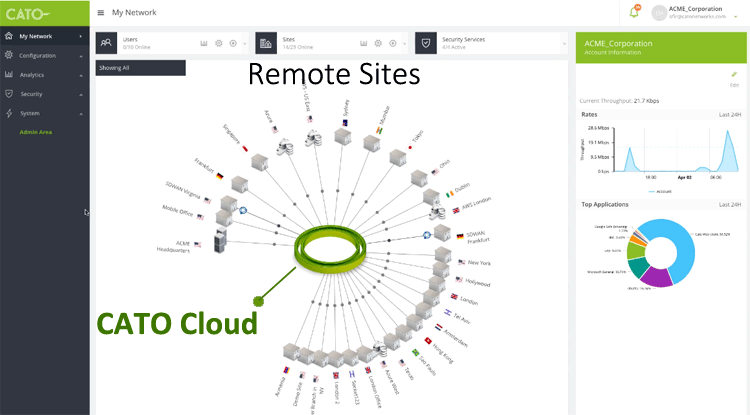
Managing a global 27 multi-location SD-WAN Network via CATO Networks
Other features to investigate for a future SD-WAN include:
SD-WAN configuration — The SD-WAN should allow for rapid site addition/removal; LDAP integration for quick addition of existing users into the SD-WAN; brief, well-documented integration process or automatic tools for cloud resource integration.
Converged configuration and reporting — Networking and security (if offered) should be tightly integrated together. A single, centralized view of all network and security events should be provided. Access-control definitions, security policies, networking policy configuration — all should be converged together. Reporting should be per site, VPN, and application.
Complete real-time visibility — The management console should provide complete visibility in realt-time into the core functioning of the SD-WAN, including the topology, connected devices, network usage statistics, as well as advanced security services.
Detailed usage metrics — Visibility into network usage should be granular, allowing IT professionals drill down into usage by VPN, location, device, user, and application. Monitoring and alerting should be provided on all networking and security events with full audit trail of all changes to system configuration and policies.
Application policy definition — The SD-WAN should allow for the creation of application policies including the specifying of the application’s importance (priority) and any relevant failover parameters.
Analytics engine and integration — An analytics engine should be provided by the product or easily integrated into the product.
Management protocols and APIs — The SD-WAN vendor should specify all northbound APIs for event correlation and user applications, and management protocols (e.g, SNMP, HTTP, XML) available for in-house integration.
Summary
This article explained what SD-WANs are and how enterprises and organizations of every size are moving towards these WAN solutions. We analyzed the problems with traditional WANs, saw the benefits of SD-WANs, SD-WAN architecture design and implementations, talked about SD-WAN deployment methods and touched heavily on SD-WAN Security, VPN, Advanced Threat Prevention, Firewall services, Mobility and Management offered by leading SD-WAN providers.
Your IP address:
18.191.200.114
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!















