Suggested Articles:

EventLog Analyzer
Unlock Deep Visibility & Insight into Windows S...
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll al...
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colaso...
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network...
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing proce...
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Networ...
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/d...
Featured Subcategories:
WireShark Articles:
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing proce...
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
Detect Brute-Force Attacks with nChronos Networ...
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/d...
Your IP address:
51.222.253.12
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fi...
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emergin...
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Aut...
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against...
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Su...
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product upda...
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single P...
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Net...
Windows Servers
Creating Windows Users and Groups with Windows 2003
In a Windows server environment, it is very important that only authenticated users are allowed to log in for security reasons. To fulfill this requirem...
Windows Servers
The Importance of a Comprehensive Backup Strategy fo...
People and companies usually adopt a backup strategy suited to the needs of their working environment. As such, there is no absolute right or wrong meth...
Windows Servers
How to Install Desktop Icons (Computer, User’s Files...
One of the first things IT Administrators and IT Managers notice after a fresh installation of Windows 2012 Server is that there are no Desktop Icons ap...
Windows Servers
Download Altaro Free VM Backup & Win a PlayStation 4...
We have some exciting news for you today!
Altaro has launched a great contest in celebration of SysAdmin Day on 27th July!
They will be giving away Am...
Popular Topics
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Network P...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and inspe...
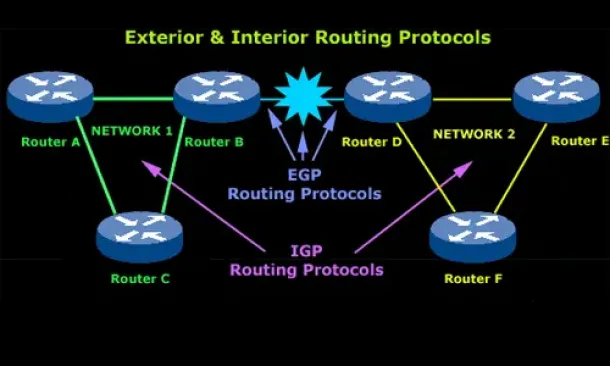
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchan...
Virtualization & VM Backup
Understanding Deduplication. Complete Guide to Dedup...
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective but al...
Windows Servers
How to Install and Configure SNMP for Windows Server...
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device support...
Cisco Services & Technologies
Introduction to Cisco VIRL – Virtual Internet Routin...
One of the most difficult things for people who are starting out in a networking career is getting their hands on the equipment. Whether you are studyin...
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA CX & ...
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and...
Cisco CallManager-CCME
Connecting & Configuring SPA8000 with UC500, 520, 54...
When it comes to connecting multiple analog phones to VoIP systems like Cisco’s Unified Communication Manager Express (CallManager Express) or UC500 ser...
Cisco Routers
Disabling Cisco Router Password Recovery Service
Most Cisco engineers are aware of the classic Password-Recovery service Cisco equipment have. If the device's credentials are lost, then performing the ...




















