Risk Management for Cisco Unified Communication Solutions - Countermeasures & Mitigation
As technology has advanced, things have become simpler yet more complex. One prime example is that of today’s communication networks. With the evolution of VoIP, the most obvious convergence is that of voice and data networks wherein both types of traffic leverage the same physical infrastructure, while retaining a possible logical network separation. While, this whole concept seems to be very exciting, there’s a big tradeoff in terms of security!
It’s unfortunate but true that, converged communication solutions are more often than not, deployed without much regard for the underlying security issues. In most cases, organizations tend to either ignore the security aspect of Unified Communication (UC) network’s security or underestimate the importance of the same. As a result a host of threats and attacks which used to be relevant to data networks now pester the voice implementation which leverages underlying data networks. Moreover, the existing security solutions which were designed for the data networks cannot adequately meet the new security challenges where voice meets data.
Unified Communications (UC) (Unified Communications is also referred to as IP Telephony) brings alongside a host of new security risks that cannot be resolved by existing security measures or solutions. While, UC risk mitigation strategies are just beginning to become known, UC threat mitigation entails significant costs or otherwise gets translated into cost of security that should be taken into account while designing the corporate UC security strategy. The first step to mitigate any risk is to know what your assets worth protecting are and what types of risks you should avert.
Let’s first understand the fundamentals of risk management.
UC Risk Management – Overview
Risk management is an art in itself as it spans multiple domains. Ideally, every asset in your UC network should be identified before going through risk management for your Cisco UC solution. This is important since it will identify what is most important to a business and where investment of time, manpower, and monetary resources will yield most favorable results. The assets that can be selected in a typical Cisco UC environment are (not limited to):
- Cisco Unified Communications Manager (CUCM)
- Cisco Unity Connection (CUC)
- Cisco Unified Presence Server (CUPS)
- Cisco Unified Communications Manager Express (CUCME)
- Cisco Unity Express (CUE)
- Cisco Voice Gateways
- Cisco Unified IP Phones (wired, wireless, softphones)
- Cisco Unified Border Element
- Cisco Catalyst Switches
- Cisco IOS Routers
- Cisco Adaptive Security Appliance (ASA)
Once the elements of your Cisco UC solution are identified, it’s time to give them their risk ratings, based on your risk appetite.
Let’s start by defining risk.
Risk – is defined as probability of something going wrong when conducting business as usual and has a negative impact.
Now, while you may know that your call-control - CUCM for example - is not secure and can be compromised, you are essentially bearing a risk that a known or an unknown threat may be realized leading to realization of the risk. In other words, you are setting up your risk appetite. Risk appetite may be classified into 3 major categories:
- Risk aversion – Averting risks, adopting security where possible, high cost affair
- Risk bearing – knowing that the network could be attacked, still bearing risk, least cost affair
- Risk conforming – knowing that the network could be attacked, bearing risk to a minimal degree by implementing most critical security measures only, a balance between risk and cost
Next comes the risk rating, i.e. how you wish to rate the criticality of an element of Cisco UC solution to the operations of your network. For example, if CUCM is under attack, what will be the impact of the same on your network? Or, if an edge router is attacked, how do you expect the communication channels to be impacted?
Each application, device and endpoint should be given a risk rating which can be low, moderate or high. The Figure below depicts risk impact vs. likelihood.
Risk Impact vs. Likelihood (ratings)
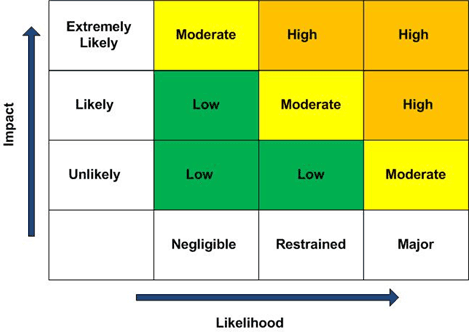 Let’s now understand the threats that lurk around your UC solution and could possibly prove detrimental to the operations of a UC network.
Let’s now understand the threats that lurk around your UC solution and could possibly prove detrimental to the operations of a UC network.
The Risks & The Threats
There’s always bad guys out there waiting to impart damage to your UC infrastructure for their financial benefit, to prove their superiority to other hackers or just for fun’s sake.
The table below gives an overview of various threats and the possibility of these threats maturing i.e. risk realization as well as the probable impact on an organization’s operations. Please note that these are the most commonly seen threats:
|
Threat Type |
Risk of Impact |
|
Confidentiality |
Leakage of sensitive information (eavesdropping) |
|
Identity theft (Spoofing) |
|
|
Integrity |
Identity theft (Spoofing) |
|
Compromised Information (Malformed packets, packet injection) |
|
|
Availability |
Service Outages (DOS, DDOS, SPIT) |
|
Lost Productivity (Bandwidth Depletion) |
|
|
Service Theft |
Excessive phone bills (Toll Fraud) |
|
Espionage (Call Hijacking) |
Let’s pay a closer visit to these threats and their risk bearings.
Eavesdropping – gives the attacker the ability to listen and record private phone conversation(s). An attacker can eavesdrop on VoIP conversations by disconnecting a VoIP phone from the wall outlet and plugging in a laptop with a softphone or packet capture software (such as Wire Shark) or by virtue of VLAN hopping attacks. Additionally, eavesdropping can be implemented using SIP proxy impersonation or registration hijacking. If this threat is realized, the risk of damage or disruption is high.
Identity Theft – Can happen at various OSI layers right from layer 2 through layer 7. Some examples are: MAC spoofing; IP spoofing; call-control / proxy / TFTP spoofing. There are freely available tools such as macmakeup, nemesis and so on which can help the attacker spoof an identity, in other words perform identity theft to trick the source or destination in a voice conversation to believe it is communicating with a legitimate person whilst it’s the attacker playing on behalf of a legitimate source. Now, a typical example of such an attack is when an attacker can spoof the MAC address of a victim’s machine and register his softphone. The attacker has the privilege equivalent to that of the victim and can conduct toll-fraud (explained later in this article) or extract information from the softphone’s web server to launch a flurry of attacks on the voice infrastructure. If this threat is realized, the risk of damage or disruption is moderate to high (depending on the privilege the attacker gains based of the victim’s profile).
Compromised Information / Loss of Information: Every business has some confidential information which, if exposed to its competitor or leaked on the internet, can prove detrimental for the business. Moreover, incorrect information passed to a destination entity can result in the business running into issues. An attacker can compromise the information in voice calls by injecting malformed packets, modifying the RTP packets, or by eavesdropping the call (discussed earlier). Packet injection or malformation attacks are difficult to detect unless an integrity method / algorithm is implemented. If this threat is realized, the risk of impact is high.
Toll fraud – This has been a classic issue since PBX days and continues to be a real nuisance in the VoIP world. An attacker finds a way to place an external call to the victim’s call-control and “hairpin” it into an outgoing call to an external destination. This could be performed using DISA, via voicemail, by a compromised IP Phone (such as a softphone), or by simply having an insider forward the calls to a desired international destination. This attack can land an organization with a skyrocketing bill in no time. The threat level of risk is high.
Denial of service – A DOS attack prevents use of the corporate UC systems, causing loss of business and productivity. An attacker can initiate a war dialer, remote dialing, or manually initiate an attack by launching multiple calls against a system. This in turn overloads the system on call-control and depletes the bandwidth. The effect can range from legit users getting the busy tone when trying to dial any number, using voice mail or IVR to system bandwidth being filled by unwanted traffic. Level of risk for this type of threat is medium.
Spam over IP Telephony (SPIT) – equivalent to email spam on data networks. It’s unsolicited and unwanted bulk messages sent / broadcast to an enterprise network’s end‐users. This causes the enterprise user’s voicemail box to be full and the endpoint to be busy with unwanted calls. These high‐volume bulk calls are very difficult to trace and inherently cause fraud and privacy violations.
Call Hijacking – UC endpoints / devices can be hijacked through a variety of hacking techniques, such as registration hijacking and call redirection. Rogue endpoints can enable a hacker to use the organization’s communication systems without authenticating to the call-control. This can lead to toll fraud and disrupt communications. Also, rogue endpoints or wireless access controllers (WLC) or wireless access points (WAP) can serve as a back door for attackers to gain entry to legitimate network zones and compromise call-control, voice messaging, presence, and other services. Level of risk for this type of threat is medium to high.
Mitigating Risks
A golden saying in the world of security is – Security is only as strongest as the weakest link!
To ensure that your Cisco UC network is secure and can deter most threats while reducing the associated risks, a multi-level security construct is required. In other words, no single security solution can restrain all threats or risks; security at multiple levels within a network i.e. at endpoint, server, application, network, perimeter, and device level helps avert a host of threats.
It’s important to treat the development of a UC risk management program as a collaborative cross‐organizational project. Any actionable risk assessment needs: a comprehensive list of threats; feasibility of realization of each threat; a prioritization of mitigation actions for each of the potential threats. It’s most important that risks be managed and mitigated in line with corporate vision and continuity of essential operations when deploying UC systems.
Following are the leading practice recommendations to mitigate risks pertinent to various threats in a Cisco UC network:
- Implement adequate physical security to restrict access to VoIP components; Voice and Data traffic segregation at VLAN level and, if possible, at firewall zone level.
- Implement VoIP enabled firewall (application layer gateway) e.g. Cisco ASA.
- If voice VLAN is propagated to a remote location, implement firewall zoning to separate inside from outside traffic.
- Disable unused switch ports.
- Implement DHCP snooping, Dynamic ARP Inspection (DAI), and port security features on Cisco Catalyst switches.
- IP Phones located in public areas such as lobby, elevator, or hotel rooms, must be separated from employee/internal network by firewalls and ideally should have their own dedicated VLAN.
- Implement 802.1x based network access control (NAC) using EAP-TLS where possible.
- Implement scavenger QoS class for P2P and other unwanted traffic.
- Secure telephony signaling using TLS and media SRTP (Cisco CAPF).
- Encrypt signaling and media traffic for endpoints, gateways, trunks, and other ecosystem applications where possible.
- Establish dedicated IDS for voice VLAN for traffic within campus and from remote sites (SPAN, RSPAN)
- Secure voice messaging ports.
- Utilize Cisco Malicious Call Identification (MCID) to tag and list malicious calls.
- Implement a call accounting/reporting system such as CAR or third party billing software to view call activity on an ongoing basis.
- Implement strong password and PIN policies as well as OTP policies.
- Use the SSO available in Cisco UC applications to suppress fraudulent admission to network.
- Configure off-hours calling policies in line with the organization’s policies.
- Configure administrative group privilege restriction levels.
- Disable PSTN to PSTN trunk transfer.
- Enable ad-hoc conferencing conclusion on exit of the initiator.
- Harden IP Phones by disabling unused features and restricting settings access.
- Sporadically review system usage reports for abnormal traffic patterns or destinations.
- Use VPN to provide a secure conduit for communication with telecommuters/remote workers. V3PN, available in Cisco IOS routers and security appliances, enables encryption of voice, video, and data traffic using IPSec. SSL VPN can also be used from VPN Phones and SSL VPN client on PC’s with softphone.
- Enforce Antivirus (on Windows based servers) and Host Intrusion Prevention System (HIPS) on Windows and Linux based servers.
- The human factor cannot be ignored. Hence, train people in your organization about their responsibility for executing enterprise risk management in accordance with established directives and protocols.
Summary
In a nutshell, there is no one-size-fits-all when it comes to securing a Cisco UC network. No two networks are alike and organizations must examine UC security from a business perspective by defining their vision, goals, policies, and patterns of usage. It’s important that the security implemented is aligned with and in compliance with applicable laws and regulations, while being effective against business risks.
Moreover, a change in risk appetite must be observed when an organization’s priorities or business processes change. A multitude of the UC security risks can be resolved by applying existing ad-hoc security measures and solutions in a planned manner as listed in previous sections. The risk management solution approach is based on evaluating the following factors in order to minimize costs and maximize mitigation of risks:
- Business Impact of realization of a risk
- Compliance requirements
- Threat surface
- Budgetary constraints
This schema is depicted in the below figure:
Risk Management Specifics for Cisco UC
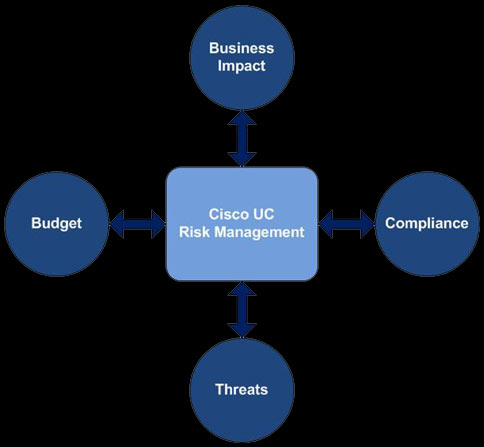
A successful UC risk management system or construct will ideally address all threats from realizing while minimizing business impact in compliance with laws and regulations, and is within budget such that the Total Cost of Ownership (TCO) decreases with time while Return on Investment (ROI) increases.
About The Author
Akhil Behl is a Senior Network Consultant with Cisco Advanced Services, focusing on Cisco Collaboration and Security architectures. He leads Collaboration and Security projects worldwide for Cisco Services and the Collaborative Professional Services (CPS) portfolio for the commercial segment. Prior to his current role, he spent 10 years working in various roles at Linksys, Cisco TAC, and Cisco AS. He holds CCIE (Voice and Security), PMP, ITIL, VMware VCP, and MCP certifications.
He has several research papers published to his credit in international journals including IEEE Xplore.
He is a prolific speaker and has contributed at prominent industry forums such as Interop, Enterprise Connect, Cloud Connect, Cloud Summit, Cisco SecCon, IT Expo, and Cisco Networkers. Akhil is also the author of Cisco Press title ‘Securing Cisco IP Telephony Networks’.
Read our exclusive interview of Akhil Behl and discover Akhil's troubleshooting techniques, guidelines in designing and securing VoIP networks, advantages and disadvantages of Cisco VoIP Telephony and much more: Interview: Akhil Behl Double CCIE (Voice & Security) #19564.
Your IP address:
18.217.107.111
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













