All-in-one protection for Microsoft 365
All-in-one protection for Microsoft 365


OpManager: Network & DC Monitoring
Monitor & Manage Network, Datacenters, endpoints & more.
Latest Articles
Free eBook Reveals Hackers Latest Attack Methods Against Microsoft’s Active Directory
 Are you ready to uncover the hidden vulnerabilities in your Active Directory (AD) environment and learn how to fortify your defenses against modern cyber threats? This comprehensive, free eBook delves deep into the critical aspects of AD security, presenting real-world attack scenarios and actionable defense strategies. Whether you're an IT administrator, security professional, or tech enthusiast, this resource is your gateway to a more secure IT infrastructure.
Are you ready to uncover the hidden vulnerabilities in your Active Directory (AD) environment and learn how to fortify your defenses against modern cyber threats? This comprehensive, free eBook delves deep into the critical aspects of AD security, presenting real-world attack scenarios and actionable defense strategies. Whether you're an IT administrator, security professional, or tech enthusiast, this resource is your gateway to a more secure IT infrastructure.
Highlights from the eBook:
- Understanding Active Directory Vulnerabilities: Gain a clear understanding of the common weaknesses in AD setups that hackers exploit, and how they can lead to devastating breaches.
- LLMNR/NBT-NS Poisoning Attacks Explained: Discover how attackers manipulate name resolution protocols to intercept sensitive data and compromise systems, and learn how to prevent these tactics.
- Defending Against SMB Relay Attacks: Learn about the mechanisms of SMB relay attacks and implement strategies to close off this dangerous avenue of attack.
- Protecting Against Kerberoasting Attacks: Get insights into the devastating power of kerberoasting, where attackers exploit service accounts to steal credentials—and how to shield your AD from this menace.
- Demystifying Domain Enumeration: Understand how attackers map out your domain to locate vulnerabilities, and explore countermeasures to disrupt their reconnaissance efforts.
- Brute Force and Password Spray Attacks: Break down these relentless attack techniques and arm yourself with tools and practices to safeguard your credentials and networks.
- Top 10 Active Directory Defense Techniques: From enforcing least-privilege principles to advanced monitoring, these strategies empower you to build a strong and resilient AD environment.

This eBook is a comprehensive guide designed to help you strengthen your AD defenses, improve incident detection, and protect your organization from emerging threats. With detailed explanations, step-by-step countermeasures, and expert insights, you’ll be equipped to identify vulnerabilities and implement effective security measures.
Don’t let your Active Directory become an easy target. Download the free eBook now to gain the knowledge and tools you need to stay one step ahead of attackers and secure your network!
How to Protect Your Business with Microsoft 365 Security Tools
 Businesses of all sizes are more and more adopting cloud-based platforms like Microsoft 365 to streamline operations, improve collaboration, and increase productivity. However, this newfound reliance on such software solutions makes these businesses prime targets for cybercriminals.
Businesses of all sizes are more and more adopting cloud-based platforms like Microsoft 365 to streamline operations, improve collaboration, and increase productivity. However, this newfound reliance on such software solutions makes these businesses prime targets for cybercriminals.
With sensitive data stored and shared across the suite, securing your Microsoft 365 environment is essential to protect your business from potential threats.
Fortunately, Microsoft 365 comes with a robust set of built-in security tools designed to safeguard your organization from cyberattacks, data breaches, and other security incidents.
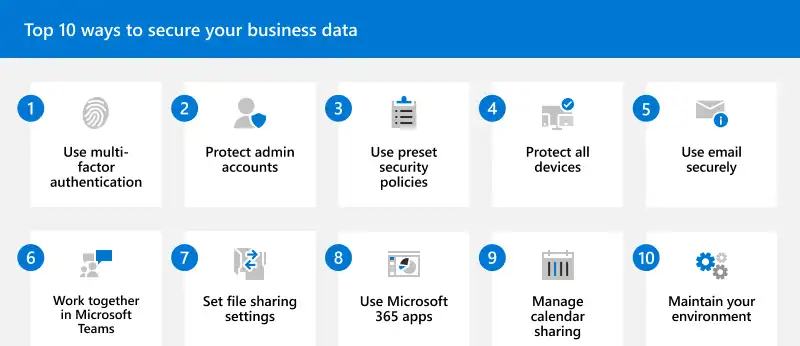
But despite that, we cannot ignore the importance of third-party Microsoft 365 total protection solutions. Without going too much into detail, these solutions enhance the already powerful native security features. But what are these features?
In this article, we’ll explore the key Microsoft 365 security tools you can use to protect your business.
Key Topics:
- Key Microsoft 365 Security Tools
- Best Practices for Leveraging Microsoft 365 Security Tools
- Conclusion
Related Articles:
- Boost Your Microsoft 365 Security with Expert Guidance and Proven Best Practices
- Empowering Users with Cyber Security Awareness Training
Key Microsoft 365 Security Tools to Protect Your Business
Microsoft Defender for Office 365
 One of the most critical security solutions within the Microsoft 365 ecosystem is Microsoft Defender for Office 365. This tool is specifically designed to protect against email-based threats such as phishing, malware, and ransomware, which are common attack vectors targeting businesses.
One of the most critical security solutions within the Microsoft 365 ecosystem is Microsoft Defender for Office 365. This tool is specifically designed to protect against email-based threats such as phishing, malware, and ransomware, which are common attack vectors targeting businesses.
Defender for Office 365 leverages real-time threat intelligence to detect and block malicious activity before it reaches your users.
Key features include:
Unlock Deep Visibility & Insight into Windows Server 2022 Logs
 This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll also discover how EventLog Analyzer provides comprehensive, helps you achieve 360-degree protection against threats targeting these logs, ensuring robust security for your server environment.
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll also discover how EventLog Analyzer provides comprehensive, helps you achieve 360-degree protection against threats targeting these logs, ensuring robust security for your server environment.
Key Topics:
- The Importance of Proactive Log Management
- Windows Server 2022 and its Key Features
- Understanding Windows Server Logs
- The Importance of Analyzing Windows Server Logs
- Benefits of Using EventLog Analyzer for Windows Server Log Analysis
- Configuring EventLog Analyzer to Connect to Windows Server
- Summary
Download your copy of EventLog Analyzer
Related Articles:
- Event Log Monitoring System: Implementation, Challenges & Standards Compliance
- Detecting Windows Server Security Threats with Advanced Event Log Analyzers
The Importance of Proactive Log Management
Did you know that threats targeting Windows Server and its logs are becoming more significant? To protect your systems, you must monitor and analyze these logs effectively. Ensuring system security, compliance, and health requires effective log management.
Administrators can ensure optimal performance by promptly identifying and resolving issues through routine log review. Log analysis also protects sensitive data by assisting in the detection of any security breaches and unwanted access. Proactive log management ultimately improves the security and dependability of the IT infrastructure as a whole.
EventLog Analyzer monitors various Windows event logs, such as security audit, account management, system, and policy change event logs. The insights gleaned from these logs are displayed in the forms of comprehensive reports and user-friendly dashboards to facilitate the proactive resolution of security issues.
Windows Server 2022 and its Key Features
Windows Server 2022 is a server operating system developed by Microsoft as a part of the Windows New Technology family. It is the most recent version of the Windows Server operating system, having been released in August 2021. Large-scale IT infrastructures can benefit from the enterprise-level administration, storage, and security features offered by Windows Server 2022. Compared to its predecessors, it has various new and improved capabilities, with an emphasis on application platform advancements, security, and hybrid cloud integrations.
Let’s take a look at a few key features of Windows Server 2022:
- Cutting-edge security features, such as firmware protection, virtualization-based security, hardware roots of trust, and secured-core servers, that protect against complex attacks.
- Improved management and integrations with Azure services via Azure Arc's support for hybrid cloud environments.
- New storage features, which include Storage Migration Service enhancements, support for larger clusters, and improvements to Storage Spaces Direct.
- Enhancements to Kubernetes, container performance, and Windows containers in Azure Kubernetes Service to improve support for containerized applications.
- Support for more powerful hardware configurations, including more memory and CPU capacity, with enhanced performance for virtualized workloads.
- File size reductions during transfers to increase efficiency and speed through the use of Server Message Block (SMB) compression.
- An integration with Azure Automanage for easier deployment, management, and monitoring of servers in hybrid and on-premises environments.
- Improved networking features, such as enhanced network security and performance as well as support for DNS over HTTPS.
- Enhanced VPN and hybrid connectivity options, such as an SMB over QUIC capability that permits safe, low-latency file sharing over the internet.
- Improvements to Windows Subsystem for Linux and tighter integration for cross-platform management, which provides better support for executing Linux workloads.
- A range of flexible deployment and licensing options, such as the usage of Azure's subscription-based licensing.
- Support for modernizing existing .NET applications and developing new applications using the latest .NET 5.0 technologies.
- Enhanced automation capabilities with the latest version of PowerShell, PowerShell 7.
Understanding Windows Server Logs
Windows Server event logs are records of events that occur within the operating system or other software running on a Windows server. You can manage, observe, and troubleshoot the server environment with the help of these logs. The logs capture numerous pieces of information, such as application problems, security incidents, and system events. By examining and evaluating these logs, administrators can ensure the security, functionality, and health of the server.
Ultimate Guide: Install Windows 11 on VMware ESXi – Easily Bypass TPM Security Requirement
 In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version 2.0 (TPM 2.0) requirement. We've also made the TPM bypass ISO image available as a free download.
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version 2.0 (TPM 2.0) requirement. We've also made the TPM bypass ISO image available as a free download.
Key Topics:
Download now your free copy of the latest V9 VM backup now.
VMware ESXi – TPM – vTPM and Windows 11
Trusted Platform Module version 2.0 (TPM 2.0) is required to run Microsoft’s Windows 11. This restricts the operating system’s installation on newer PCs, it also means users with older hardware are likely to be forced to upgrade. While the virtualization world is often more forgiving when it comes to hardware requirements, trying to install Windows 11 on VMware’s ESXi platform usually present the error: “This PC can’t run Windows 11”:
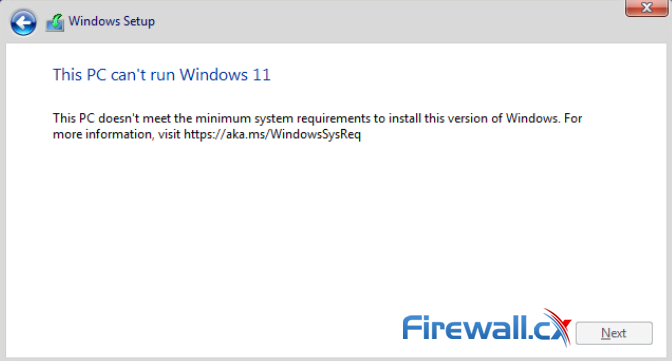 Windows 11 Installation Error in VMware ESXi
Windows 11 Installation Error in VMware ESXi
Running Windows 11 as a virtual machine on VMware ESXi requires a virtual Trusted Platform Module (vTPM) present. For more details on Microsoft Windows 11 requirements see, https://docs.microsoft.com/en-us/windows/whats-new/windows-11-requirements.
While VMware supports vTPM and doesn’t require a physical TPM 2.0 chip, to use it, you need to configure a number of different services, depending on your VMware Platform version, including vCenter, vSphere Native Key Provider and more, making it a complicated task – especially for those running home labs. For more details see, https://core.vmware.com/resource/windows-11-support-vsphere#section2.
The next steps will take you through downloading the TPM ISO image used to bypass the Windows TPM check.
Your IP address:
135.181.29.24
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Featured Categories:
Top Picks:
Free Webinar: Learn How Zero-Trust & Cloud Tech...
Differences Between VMware vSphere, vCenter, ES...

How to Manually Download, Import & Install PAN-...
Palo Alto Firewall Application-based Policy Enf...
Key Features of a True Cloud-Native SASE Service. Setting the Right Expectations
Converged SASE Backbone – How Leading SASE Provider, Cato Networks, Reduced Jitter/Latency and Packet Loss by a Factor of 13!
Configuring A SASE Unified Network: Data centers, Remote Sites, VPN Users, and more
The Need for a Converged SASE Platform. Converging Network & Security Services with Catonetworks SASE Platform

VTP Pruning

VLAN InterSwitch Link (ISL) Protocol Analysis

VTP Introduction & Modes

Static VLANs
Hybrid Routing Protocols - Advantages and Disadvantages - Comparison
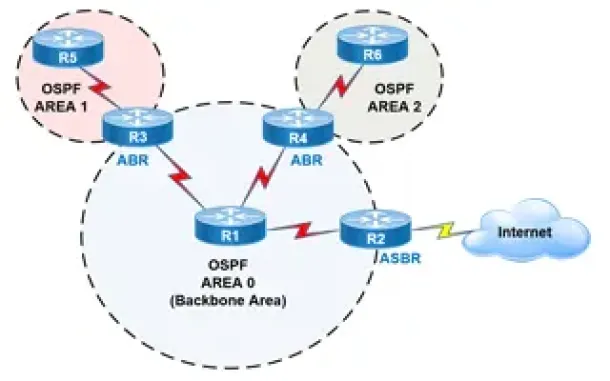
OSPF - Part 2: How OSPF Protocol Works & Basic Concepts: OSPF Neighbor, Topology & Routing Table, OSPF Areas & Router Roles, Theory & Overview
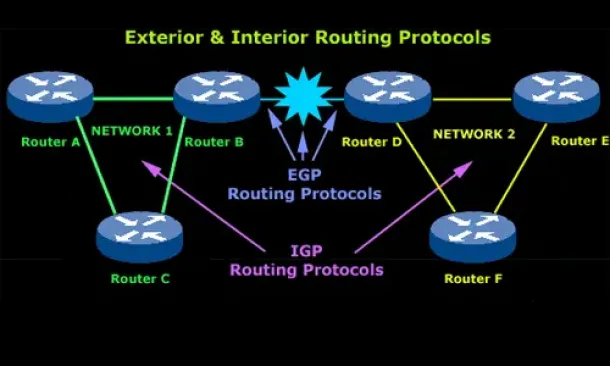
Introduction to Routing Protocols